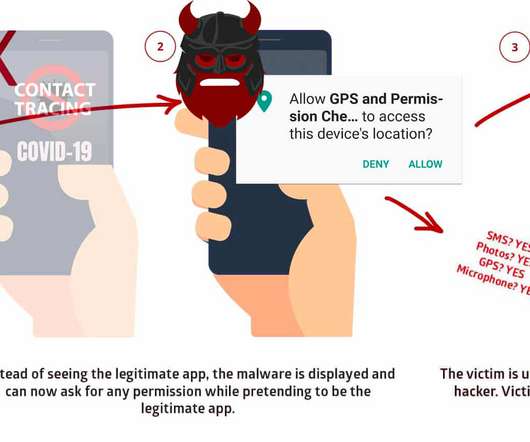
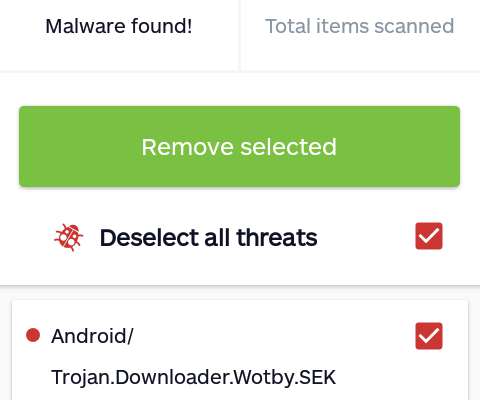
Microsoft released out-of-band Windows fixes for 2 RCE issues
Security Affairs
OCTOBER 18, 2020
.” The CVE-2020-17022 vulnerability affects all devices running Windows 10, version 1709 or later, and a vulnerable library version. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. Copyright (C) 2014 Media.net Advertising FZ-LLC All Rights Reserved -->. Pierluigi Paganini.




























Let's personalize your content