New Gallmaker APT group eschews malware in cyber espionage campaigns
Security Affairs
OCTOBER 10, 2018
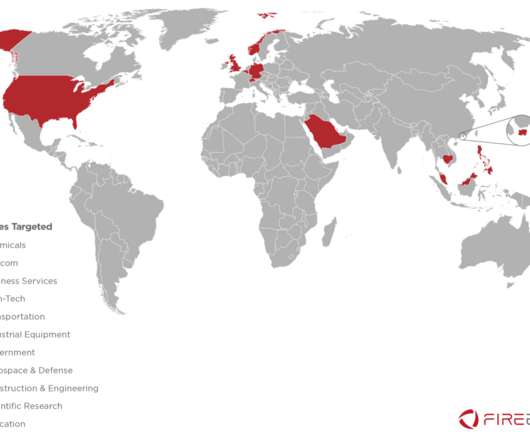
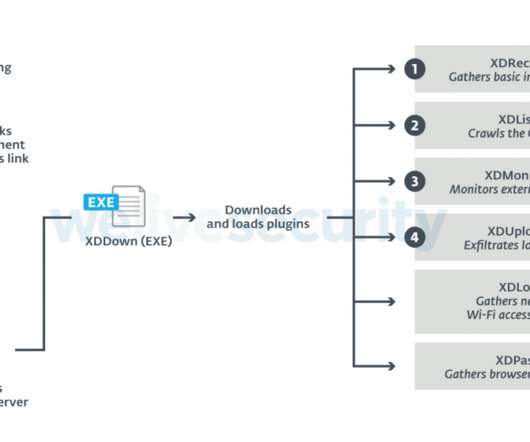
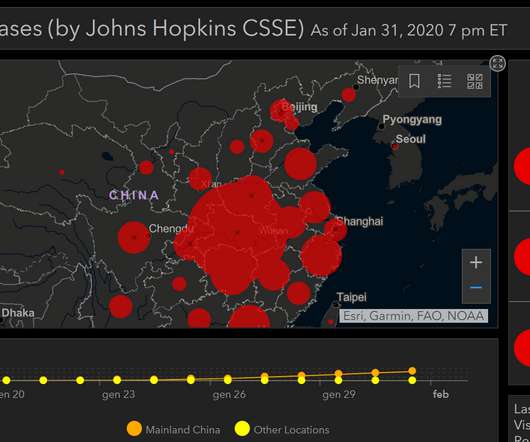
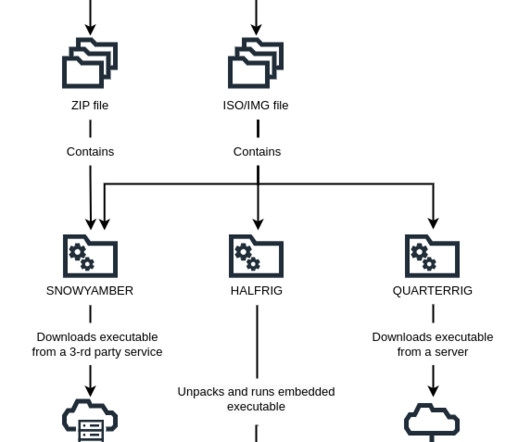
A previously unknown cyber espionage group, tracked as Gallmaker, has been targeting entities in the government, military and defense sectors since at least 2017. A new cyber espionage group tracked as Gallmaker appeared in the threat landscape. ” continues Symantec. Pierluigi Paganini.



































Let's personalize your content