What is credential stuffing? And how to prevent it?
Security Affairs
MARCH 29, 2022
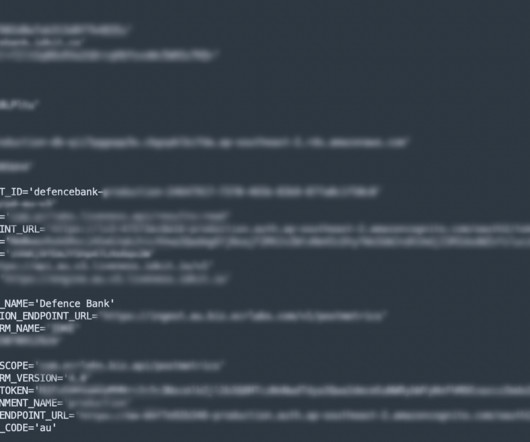
Earmarked by the FBI as a particular threat to the financial service industry just over a year ago, the increase of internet traffic, data breaches and API usage all contribute to the perfect conditions for successful credential stuffing attacks. How to stop credential stuffing attacks. And how to prevent it?






























Let's personalize your content