“gitgub” malware campaign targets Github users with RisePro info-stealer
Security Affairs
MARCH 17, 2024
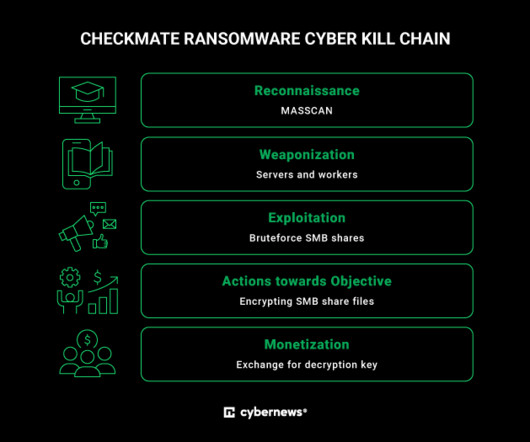
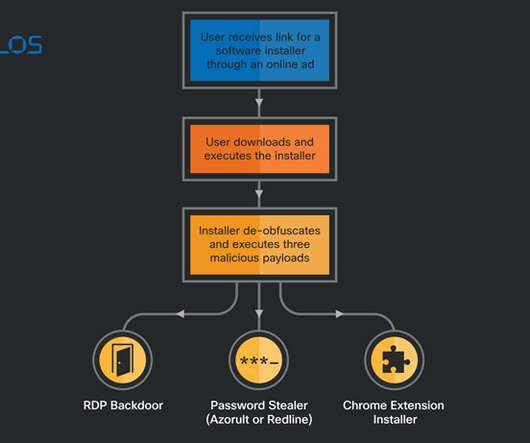
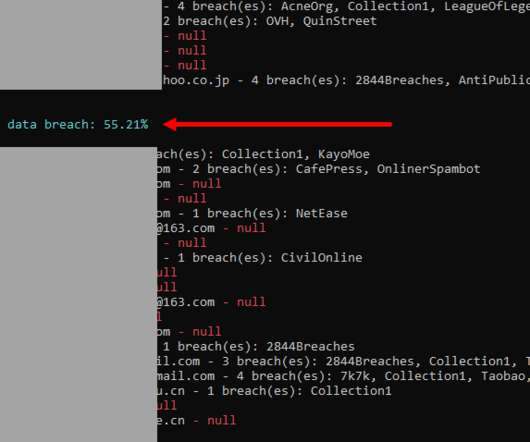
The experts noticed that this campaign was named “gitgub” by its operators. The experts created a threat-hunting tool that allowed them to identify the repositories involved in this campaign. “We identified at least 13 such repositories belonging to a RisePro stealer campaign that was named “gitgub” by the threat actors. .”


























Let's personalize your content