Russia-linked Gamaredon APT targeted a western government entity in Ukraine
Security Affairs
FEBRUARY 4, 2022
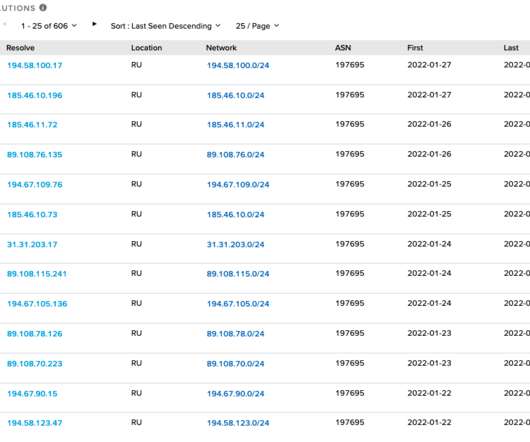
The Russia-linked Gamaredon APT group attempted to compromise an unnamed Western government entity in Ukraine. In Mid January the Ukrainian government was hit with destructive malware, tracked as WhisperGate , and several Ukrainian government websites were defaced by exploiting a separate vulnerability in OctoberCMS.



























Let's personalize your content