Tricky Phish Angles for Persistence, Not Passwords
Krebs on Security
JANUARY 7, 2020
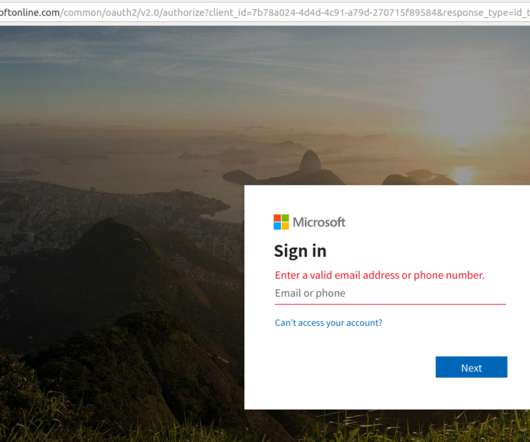
Late last year saw the re-emergence of a nasty phishing tactic that allows the attacker to gain full access to a user’s data stored in the cloud without actually stealing the account password. Still, this phishing tactic is worth highlighting because recent examples of it received relatively little press coverage.























Let's personalize your content