Adventures in cyber litigation: Frozen crypto-assets and the role of cyber insurance
Data Protection Report
FEBRUARY 27, 2020
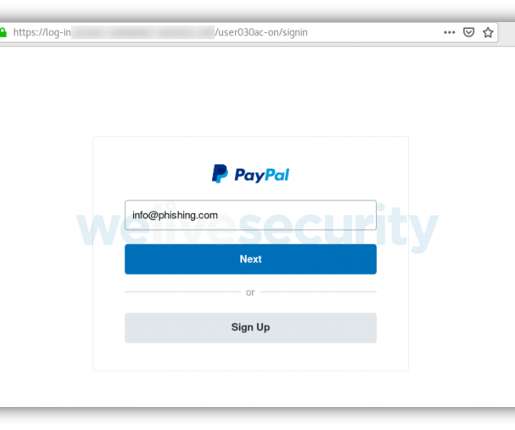
Given the level of interest in the case, we have prepared a deeper-dive into the facts and the implications of the decision, with a focus on the important role played in the case by cyber insurance. For some time, cyber exposure has been at or near the top of every major company’s risk register. This is set out below.
























Let's personalize your content