International Worker’s Day and the Female Workforce
Unwritten Record
MAY 3, 2022
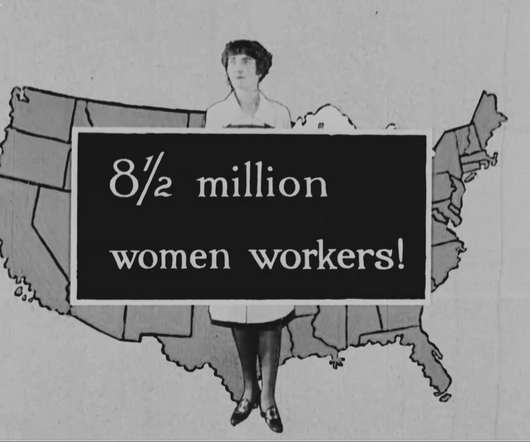
One of the most extensive groups of labor records comes from the Department of Labor found in Record Group 174: General Records of the Department of Labor. In NARA’s holdings, films produced by the Department of Labor are filed among several record groups mirroring the agency’s topic specific organization and functions.






























Let's personalize your content