Microsoft links Cadet Blizzard APT to Russia’s military intelligence GRU
Security Affairs
JUNE 14, 2023
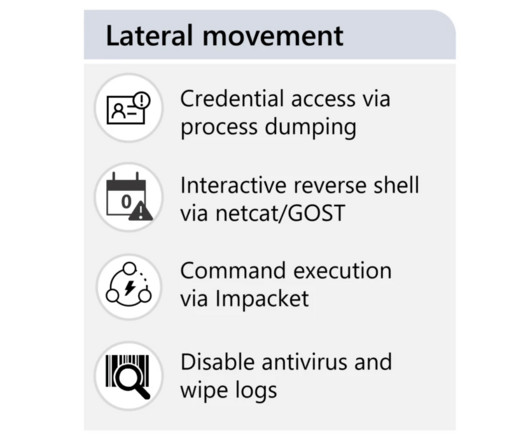
The IT giant pointed out that Cadet Blizzard is distinct from other known APT groups operating under the control of the Russian military intelligence GRU, such as Forest Blizzard ( STRONTIUM ) and Seashell Blizzard (IRIDIUM). Unlike other Russia-linked APT group, CadetBlizzard operations are extremely disruptive.










































Let's personalize your content