FBI obtained 7,000 LockBit decryption keys, victims should contact the feds to get support
Security Affairs
JUNE 6, 2024
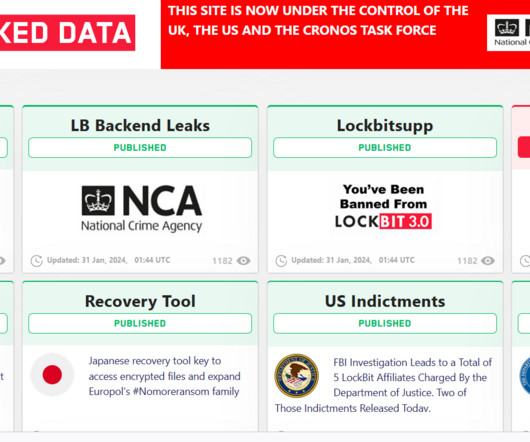
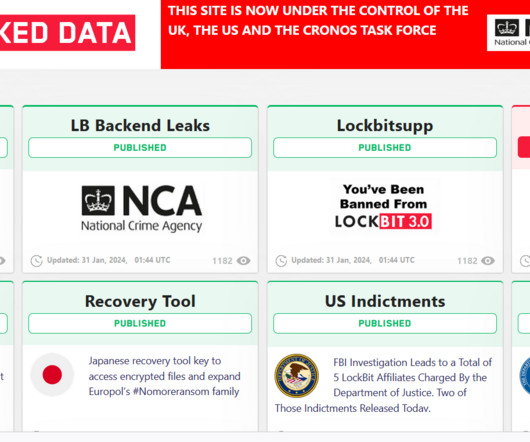
The FBI is inviting victims of LockBit ransomware to come forward because it has obtained over 7,000 LockBit decryption keys that could allow them to recover their encrypted data for free. The NCA reached out to victims based in the UK providing support to help them recover encrypted data.


















Let's personalize your content