How to Decrypt Ransomware Files – And What to Do When That Fails
eSecurity Planet
OCTOBER 18, 2022
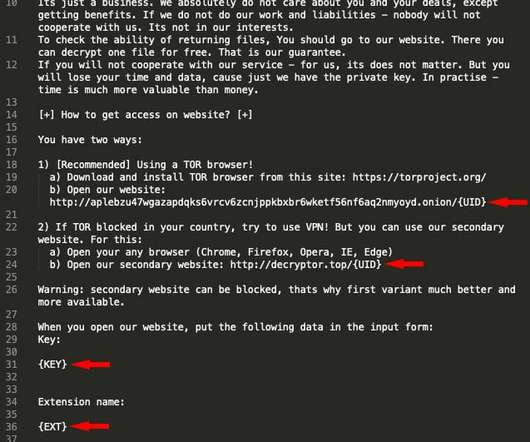
The bad news is it doesn’t work most of the time: Paid ransom decryption tools and keys don’t always work. Free decryption tools don’t always work. Paid decryption tools don’t always work. Also read: Best Backup Solutions for Ransomware Protection How One Company Survived a Ransomware Attack Without Paying the Ransom.


















































Let's personalize your content