Apple Tracks You More Than You Think
WIRED Threat Level
NOVEMBER 26, 2022
Plus: WikiLeaks’ website is falling apart, tax websites are sending your data to Facebook, and cops take down a big phone-number-spoofing operation.

WIRED Threat Level
NOVEMBER 26, 2022
Plus: WikiLeaks’ website is falling apart, tax websites are sending your data to Facebook, and cops take down a big phone-number-spoofing operation.

IG Guru
NOVEMBER 30, 2022
Check out the article here.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

IT Governance
DECEMBER 1, 2022
Welcome to our November 2022 review of data breaches and cyber attacks. We identified 95 security incidents throughout the month, accounting for 32,051,144 breached records. Almost half of that figure comes from two incidents. The first was a data breach at Twitter, in the latest PR disaster for the social media giant. Reports emerged late last week that user records were stolen using an API vulnerability that has since been fixed.

Krebs on Security
NOVEMBER 28, 2022
A recent scoop by Reuters revealed that mobile apps for the U.S. Army and the Centers for Disease Control and Prevention (CDC) were integrating software that sends visitor data to a Russian company called Pushwoosh , which claims to be based in the United States. But that story omitted an important historical detail about Pushwoosh: In 2013, one of its developers admitted to authoring the Pincer Trojan , malware designed to surreptitiously intercept and forward text messages from Android mob

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Data Breach Today
NOVEMBER 29, 2022
Firms Fear that Involving Police in Response Will Have Regulatory Consequences U.K. businesses shy from involving police in cyber incident response for fear of regulatory consequences, lawmakers sitting on Parliament's Joint Committee on National Security Strategy heard. Allowing businesses to anonymously disclose incidents would result in more data, suggested a witness.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Data Breach Today
NOVEMBER 28, 2022
But Information Compiled by Other Attackers May Involve Millions of Other Accounts Information amassed on 5.4 million Twitter users by an attacker who abused one of the social network's APIs has been dumped online for free. While Twitter confirmed that breach, a researcher suggests other attackers also abused the feature to amass information for millions of other users.
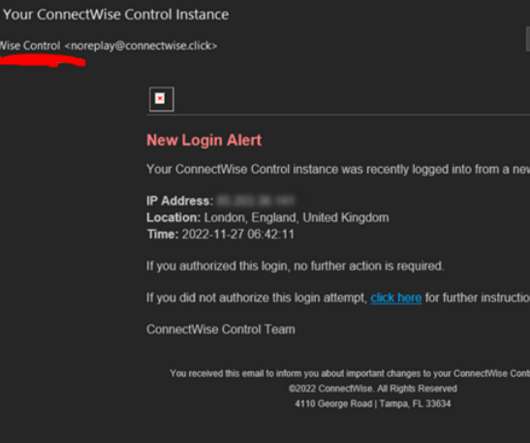
Krebs on Security
DECEMBER 1, 2022
ConnectWise , which offers a self-hosted, remote desktop software application that is widely used by Managed Service Providers (MSPs), is warning about an unusually sophisticated phishing attack that can let attackers take remote control over user systems when recipients click the included link. The warning comes just weeks after the company quietly patched a vulnerability that makes it easier for phishers to launch these attacks.

Dark Reading
NOVEMBER 30, 2022
The simplicity and profitability of these attacks continue to appeal to threat actors a decade later.

Security Affairs
NOVEMBER 29, 2022
In today’s technological world, educating people about cybersecurity awareness is an absolute necessity. According to one report , 82% of data breaches involved the human element, from social attacks to misuse of technologies. These errors are not always entirely preventable, as some level of human error is inevitable, but proper training in cybersecurity awareness can greatly decrease the likelihood of human mistakes leading to data breaches.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Data Breach Today
DECEMBER 2, 2022
Some Customers at Risk of Identity Theft, South Staffordshire Water Belatedly Warns Is a four-month delay between learning your systems were breached and notifying affected customers acceptable? After spotting an attack in August, private utility South Staffordshire Water in England is only beginning to alert customers that they're at risk of identity theft.

Hunton Privacy
NOVEMBER 30, 2022
On November 15, 2022, the Italian Supreme Court held that an Italian court or competent data protection authority has jurisdiction to issue a global delisting order. A delisting order requires a search engine to remove certain search results about individuals if the data subject’s privacy interests prevail over the general right to expression and information, and the economic interest of the search engine.

WIRED Threat Level
NOVEMBER 28, 2022
Google provided investigators with location data for more than 5,000 devices as part of the federal investigation into the attack on the US Capitol.

Security Affairs
DECEMBER 2, 2022
Qualys researchers demonstrated how to chain a new Linux flaw with two other two issues to gain full root privileges on an impacted system. Researchers at the Qualys’ Threat Research Unit demonstrated how to chain a new Linux vulnerability, tracked as CVE-2022-3328 , with two other flaws to gain full root privileges on an affected system. The vulnerability resides in the snap-confine function on Linux operating systems, a SUID-root program installed by default on Ubuntu.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Data Breach Today
DECEMBER 1, 2022
Feds Warn Impermissible Disclosures of Patient Health Data is Prohibited Federal regulators issued a warning to healthcare entities and their tech vendors that the use of tracking code embedded in patient portals that transmits patient information to third-parties could be a violation of HIPAA, and punishable with monetary fines.

Schneier on Security
NOVEMBER 28, 2022
Laptop technicians routinely violate the privacy of the people whose computers they repair: Researchers at University of Guelph in Ontario, Canada, recovered logs from laptops after receiving overnight repairs from 12 commercial shops. The logs showed that technicians from six of the locations had accessed personal data and that two of those shops also copied data onto a personal device.

eSecurity Planet
DECEMBER 1, 2022
The Wiz Research Team recently discovered a supply chain vulnerability in IBM Cloud that they say is the first to impact a cloud provider’s infrastructure. In a dramatic flair, they named the flaw Hell’s Keychain. The security issues were reported to IBM Cloud in late August, and were patched in early September. Before it was patched, an attacker with knowledge of the vulnerability could run malicious code and modify data being stored by any IBM Cloud customer using PostgreSQL.
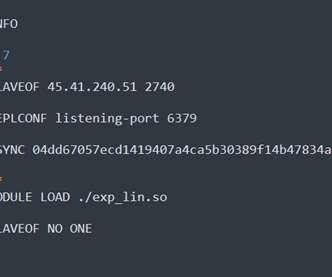
Security Affairs
DECEMBER 1, 2022
Redigo is a new Go-based malware employed in attacks against Redis servers affected by the CVE-2022-0543 vulnerability. Researchers from security firm AquaSec discovered a new Go-based malware that is used in a campaign targeting Redis servers. Threat actors are exploiting a critical vulnerability, tracked as CVE-2022-0543 , in Redis (Remote Dictionary Server) servers.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Data Breach Today
DECEMBER 1, 2022
Australian Information Commissioner Will Investigate Insurer's Security Practices The Russia-based ransomware gang behind the hack of Australia's largest private health insurer says it posted a full set of stolen data. The Australian Information Commissioner said it will probe the insurer's personal information handling practices.

KnowBe4
NOVEMBER 30, 2022
Every holiday season brings on an increase in gift card scams. Most people love to buy and use gift cards. They are convenient, easy to buy, easy to use, easy to gift, usually allow the receiver to pick just what they want, and are often received as a reward for doing something. The gift card market is estimated in the many hundreds of BILLIONS of dollars.
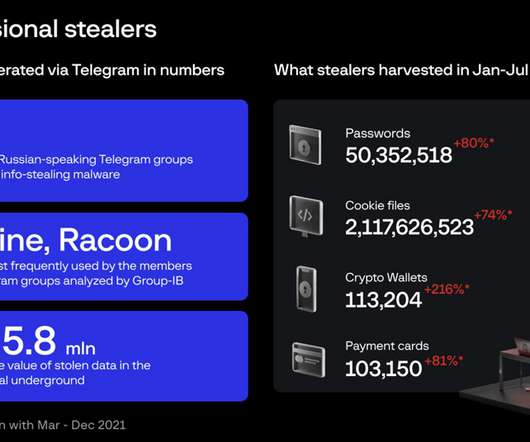
eSecurity Planet
NOVEMBER 29, 2022
Group-IB cybersecurity researchers recently identified several Russian-speaking cybercrime groups offering infostealing malware-as-a-service (MaaS), resulting in the theft of more than 50 million passwords thus far. The cybercrime groups are using Raccoon and Redline malware to steal login credentials for Steam, Roblox, Amazon and PayPal, as well as payment records and crypto wallet information.
Security Affairs
NOVEMBER 28, 2022
Amazon Web Services (AWS) fixed a cross-tenant vulnerability that could have allowed attackers to gain unauthorized access to resources. Amazon Web Services (AWS) has addressed a cross-tenant confused deputy problem in its platform that could have allowed threat actors to gain unauthorized access to resources. The problem was reported to the company by researchers from Datadog on September 1, 2022, and the bug was solved on September 6.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Data Breach Today
NOVEMBER 30, 2022
One Brooklyn Health Systems Three Hospitals Systems Affected by Nov. 19 Hack As three Brooklyn safety net hospitals grapple with the aftershocks of a Nov. 19 cyber incident, sources say other area hospitals are complaining about a lack of transparency. One Brooklyn Health System has been tight-lipped about the cause of the outage, which is suspected to involve ransomware.

John Battelle's Searchblog
NOVEMBER 28, 2022
There’s so much to say about what’s happening at Twitter, but I’m going to start with one word: “Hardcore.” That’s what Elon said he wants from all his employees going forward – a “hardcore” mentality, a coder-first culture, a sleep-at-the-office-and-pound-Red-Bull kind of sensibility. I’m pretty familiar with this culture – an earlier, less toxic version of it pervaded the pre-Elon tech world, a culture I reported on at Wired , t

Dark Reading
DECEMBER 1, 2022
The threat actor behind an August intrusion used data from that incident to access customer data stored with a third-party cloud service provider, and affiliate GoTo reports breach of development environment.
Security Affairs
NOVEMBER 28, 2022
ESET announced the discovery of a vulnerability impacting Acer laptops that can allow an attacker to deactivate UEFI Secure Boot. ESET researchers announced in a series of tweets the discovery of a vulnerability impacting Acer laptops, the issue can allow an attacker to deactivate UEFI Secure Boot. The experts explained that the flaw, tracked as CVE-2022-4020 , is similar to the Lenovo vulnerabilities the company disclosed earlier this month.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Data Breach Today
NOVEMBER 28, 2022
Fine Tied to Data Scrapping Incident Revealed in 2021 Facebook will pay a 265 million euro fine to the Irish data protection authority to resolve a 2021 incident when the scrapped data of 533 million users appeared online. The data contained names, phone numbers and birth dates. Facebook says it takes active measures against data scrapping.
eSecurity Planet
NOVEMBER 29, 2022
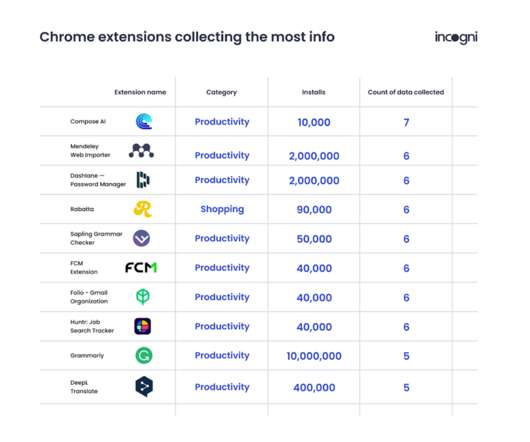
In a recent study of 1,237 Chrome extensions with a minimum of 1,000 downloads, Incogni researchers found that nearly half ask for permissions that could potentially expose personally identifiable information (PII), distribute adware and malware , or even log everything users do online, including accessing passwords and financial data. Almost half (48.66 percent) of all Chrome extensions have a High or Very High risk impact due to permissions required at installation, according to Incogni, and o

KnowBe4
NOVEMBER 28, 2022
It’s easy to think of the typical online holiday scam as something that affects mostly individuals. Sad, maybe, and unfortunate, but not something that might seriously threaten a business, or another organization.
Let's personalize your content