IoT Attacks Skyrocket, Doubling in 6 Months
Threatpost
SEPTEMBER 6, 2021
The first half of 2021 saw 1.5 billion attacks on smart devices, with attackers looking to steal data, mine cryptocurrency or build botnets.

Threatpost
SEPTEMBER 6, 2021
The first half of 2021 saw 1.5 billion attacks on smart devices, with attackers looking to steal data, mine cryptocurrency or build botnets.

eSecurity Planet
SEPTEMBER 10, 2021
In a year where ransomware has raised the alert levels everywhere, the go-to answer from many is redundancy through offline, remote backups – but are they enough? Backups are a critical component of any enterprise cybersecurity posture, but they are not an airtight strategy. Like any other digital machine, backup systems are vulnerable to data loss and compromise.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Troy Hunt
SEPTEMBER 9, 2021
111 years ago almost to the day, a murder was committed which ultimately led to the first criminal trial to use fingerprints as evidence. We've all since watched enough crime shows to understand that fingerprints are unique personal biometric attributes and to date, no two people have ever been found to have a matching set. As technology has evolved, fingers (and palms and irises and faces) have increasingly been used as a means of biometric authentication.
Data Breach Today
SEPTEMBER 8, 2021
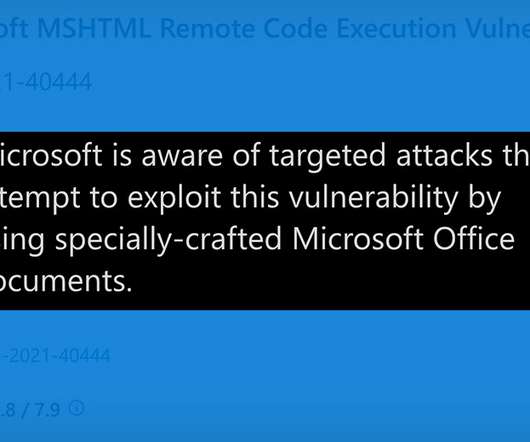
Workarounds Detailed to Block Active Attack; Microsoft Has Yet to Release Patches Attackers are actively exploiting a flaw in Microsoft Windows for which no patch is yet available. Microsoft has issued workarounds and mitigations designed to block the zero-day attack for the flaw in the MSHTML browsing engine, which is being exploited via malicious Microsoft Office documents.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Krebs on Security
SEPTEMBER 8, 2021
Microsoft Corp. warns that attackers are exploiting a previously unknown vulnerability in Windows 10 and many Windows Server versions to seize control over PCs when users open a malicious document or visit a booby-trapped website. There is currently no official patch for the flaw, but Microsoft has released recommendations for mitigating the threat.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
Security Affairs
SEPTEMBER 9, 2021
The massive DDoS attack that has been targeting the internet giant Yandex was powered b a completely new botnet tracked as M?ris. The Russian Internet giant Yandex has been targeting by the largest DDoS attack in the history of Runet, the Russian Internet designed to be independent of the world wide web and ensure the resilience of the country to an internet shutdown.
Data Breach Today
SEPTEMBER 6, 2021
Revenue, Size, Geography and Level of Access Help Determine Sale Price for Access The most sought-after type of victim for ransomware-wielding attackers is a large, U.S.-based business with at least $100 million in revenue, not operating in the healthcare or education sector, with remote access available via remote desktop protocol or VPN credentials, threat intelligence firm Kela reports.
Krebs on Security
SEPTEMBER 10, 2021
On Thursday evening, KrebsOnSecurity was the subject of a rather massive (and mercifully brief) distributed denial-of-service (DDoS) attack. The assault came from “ Meris ,” the same new “Internet of Things” (IoT) botnet behind record-shattering attacks against Russian search giant Yandex this week and internet infrastructure firm Cloudflare earlier this summer.

Troy Hunt
SEPTEMBER 6, 2021
For the last few years, I've been welcome national governments to Have I Been Pwned (HIBP) and granting them full and free access to domain-level searches via a dedicated API. Today, I'm very happy to welcome the Czech Republic's National Cyber and Information Security Agency who can now query their government domains along with the 26 other nations that have come before them.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.
Security Affairs
SEPTEMBER 6, 2021
A Russian man accused of being a member of the infamous TrickBot gang was arrested while trying to leave South Korea. A Russian man accused of being a member of the TrickBot gang was arrested last week at the Seoul international airport. The man has remained stuck in the Asian country since February 2020 due to the COVID-19 lockdown imposed by the local government and the cancelation of international travel.

Data Breach Today
SEPTEMBER 4, 2021
Flaws Fixed, Mitigations Issued for Discontinued Devices SEC Consult reportedly found multiple vulnerabilities in Moxa devices used in critical infrastructures including railways, manufacturing, cellular and heavy industries. Moxa has confirmed patching 60 vulnerabilities in its latest firmware update and issued mitigation advice for discontinued devices.
Krebs on Security
SEPTEMBER 6, 2021
In May 2015, KrebsOnSecurity briefly profiled “ The Manipulaters ,” the name chosen by a prolific cybercrime group based in Pakistan that was very publicly selling spam tools and a range of services for crafting, hosting and deploying malicious email. Six years later, a review of the social media postings from this group shows they are prospering, while rather poorly hiding their activities behind a software development firm in Lahore that has secretly enabled an entire generation of

Hunton Privacy
SEPTEMBER 9, 2021
On August 19, 2021, the Belgian Council of State confirmed a decision of the regional Flemish Authorities to contract with an EU branch of a U.S. company using Amazon Web Services (“AWS”). The decision was made in the context of a tender granted by the Flemish Authorities to a company that used AWS cloud services. An unsuccessful tender participant had challenged the outcome of the tender process before the Council of State, deploying several arguments, including that a lack of appropriate safeg

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.
Security Affairs
SEPTEMBER 5, 2021
The Irish Data Protection Commission has fined WhatsApp €225 million over data sharing transparency for European Union users’ data with Facebook. The Irish Data Protection Commission has fined WhatsApp €225 million for the lack of transparency on how it shares European Union users’ data with Facebook companies. The instant messaging company violated the actual General Data Protection Regulation (GDPR). “The Data Protection Commission (DPC) has today announced a conclusion to a

Data Breach Today
SEPTEMBER 8, 2021
Experts Say Social Engineering Continues to Drive Illicit Activity The U.S. SEC in a new advisory warns against schemes targeting digital assets. Security experts say that with social engineering attempts on the rise, individuals and organizations must defend against related scams and other "get rich quick" schemes.

IT Governance
SEPTEMBER 8, 2021
Organisations that adopted hybrid working during the pandemic have had to adjust many policies and processes, but one that they may have overlooked is their CIR (cyber incident response) plan. Before the pandemic, you could safely assume that most employees were based in the office and therefore a controlled environments. That made planning for disruptions comparatively straightforward: you knew where everyone was located, you had complete visibility over your threat landscape and you could comm

eSecurity Planet
SEPTEMBER 10, 2021
Palo Alto Networks (PANW) is bringing its enterprise-class security to small business and home markets with Okyo , a Wi-Fi 6 hardware device announced today. At $349 a year, the security and router system seems attractively priced for small businesses and companies looking to secure remote workers , who have surged in number since the start of the Covid pandemic 18 months ago.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Security Affairs
SEPTEMBER 10, 2021
Microsoft has fixed the Azurescape issue, a flaw in Azure Container Instances that allows to take over containers of other platform users. Microsoft has addressed a vulnerability in Azure Container Instances (ACI) called Azurescape that could have allowed a malicious container to take over containers belonging to other users. An attacker could exploit the vulnerability to execute commands in the containers of other users and access to their data.

Data Breach Today
SEPTEMBER 8, 2021
Classes Canceled as the University's IT Staff Repairs Damage Howard University canceled classes Tuesday in the wake of a ransomware attack it first detected on Friday, the university has announced. There is no evidence the attackers accessed or exfiltrated personal information, the school says.

Threatpost
SEPTEMBER 10, 2021
With so many people still working from home, cybercriminals are trying to cash in. Cyberattacks have increased 300% and the risk of losing important data or being compromised is much greater at home. Here are five recommendations for securing your home office.

eSecurity Planet
SEPTEMBER 7, 2021
Zero day threats can be the source of some of the most dangerous kinds of cyberattacks. Zero day attacks take advantage of vulnerabilities that haven’t been discovered or are not publicly known yet. One of the things that makes these threats so dangerous is that they often come without warning, posing a huge risk to the companies or individuals at stake.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.
Security Affairs
SEPTEMBER 4, 2021
FIN7 cybercrime gang used weaponized Windows 11 Alpha-themed Word documents to drop malicious payloads, including a JavaScript backdoor. Anomali Threat Research experts have monitored recent spear-phishing attacks conducted by financially motivated threat actor FIN7. The messages used weaponized Windows 11 Alpha-themed Word documents with Visual Basic macros to drop malicious payloads, including a JavaScript backdoor, in an attack aimed at a US point-of-sale (PoS) service provider.
Data Breach Today
SEPTEMBER 8, 2021
NZ CERT: Intermittent Disruptions at Financial Organizations New Zealand's Computer Emergency Response Team says it is aware of ongoing distributed denial-of-service attacks that have disrupted services at several organizations in the country, including some financial institutions and the national postal service.

The Guardian Data Protection
SEPTEMBER 8, 2021
Exclusive: national and local governments using targeted ads on search engines and social media A new form of “influence government”, which uses sensitive personal data to craft campaigns aimed at altering behaviour has been “supercharged” by the rise of big tech firms, researchers have warned. National and local governments have turned to targeted advertisements on search engines and social media platforms to try to “nudge” the behaviour of the country at large, the academics found.

Threatpost
SEPTEMBER 10, 2021
Threat actors accessed the organization’s proprietary project management software, Umoja, in April, accessing the network and stealing info that can be used in further attacks.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Security Affairs
SEPTEMBER 8, 2021
Microsoft warns of a zero-day vulnerability in Internet Explorer that is actively exploited by threat actors using weaponized Office docs. Microsoft warns of a zero-day vulnerability (CVE-2021-40444) in Internet Explorer that is actively exploited by threat actors to hijack vulnerable Windows systems. Microsoft did not share info about the attacks either the nature of the threat actors.

Data Breach Today
SEPTEMBER 10, 2021
Threat Actors Offered Credentials for UN's ERP Software; NATO Hit as Well The United Nations says on Thursday that its networks were accessed by intruders earlier this year, which lead to follow-on intrusions. Cybercrime analysts say they warned the agency when access credentials to a U.N. enterprise resource planning software system were seen offered for sale.

Hunton Privacy
SEPTEMBER 7, 2021
On August 9, 2021, Baltimore joined Portland, Oregon and New York City in enacting a local ordinance regulating the private sector’s use of facial recognition technology. Baltimore’s ordinance will become effective on September 8, 2021. Read our earlier post for more details about Baltimore’s ban on the use of facial recognition technology by private entities and individuals within its city limits.
Let's personalize your content