Tech CEO Sentenced to 5 Years in IP Address Scheme
Krebs on Security
OCTOBER 17, 2023
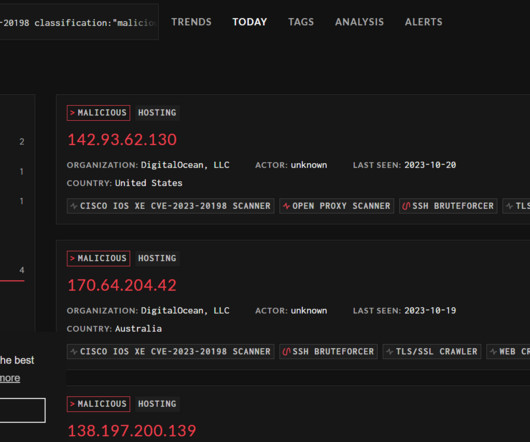
Amir Golestan , the 40-year-old CEO of the Charleston, S.C. based technology company Micfo LLC , has been sentenced to five years in prison for wire fraud. Golestan’s sentencing comes nearly two years after he pleaded guilty to using an elaborate network of phony companies to secure more than 735,000 Internet Protocol (IP) addresses from the American Registry for Internet Numbers (ARIN), the nonprofit which oversees IP addresses assigned to entities in the U.S., Canada, and parts of the Ca





































Let's personalize your content