SUPERNOVA, a Backdoor Found While Investigating SolarWinds Hack
Security Affairs
DECEMBER 21, 2020
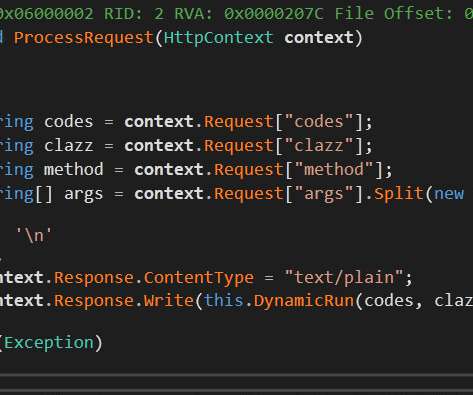
While investigating the recent SolarWinds Orion supply-chain attack security researchers discovered another backdoor, tracked SUPERNOVA. The investigation of the SolarWinds Orion supply-chain attack revealed the existence of another backdoor that was likely used by a separate threat actor.





































Let's personalize your content