Experts Demonstrated How to Hack a Utility and Take Over a Smart Meter
Security Affairs
APRIL 19, 2021
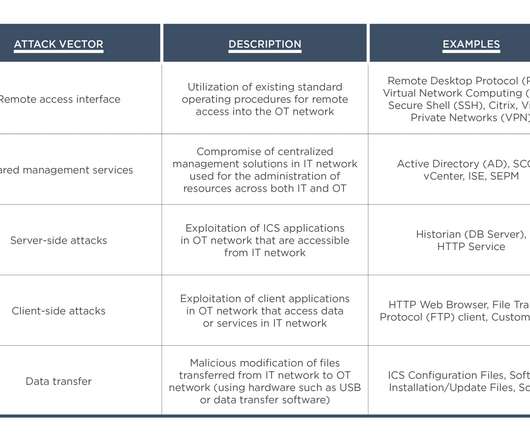
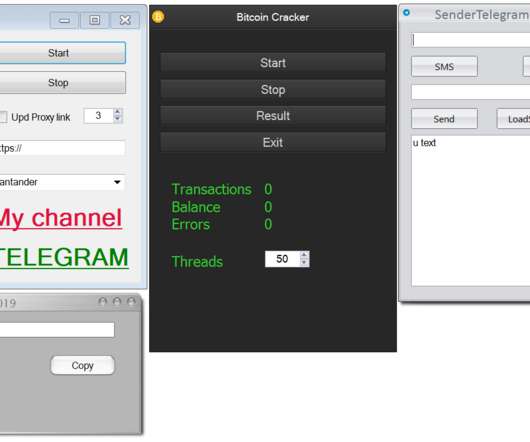
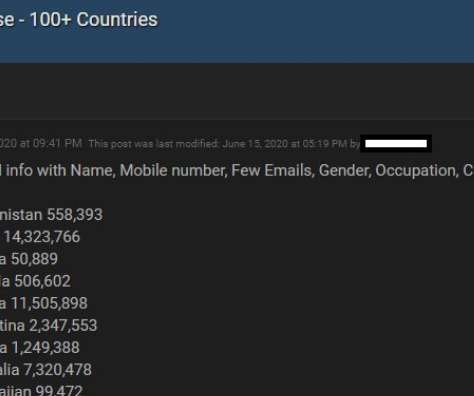
Researchers from the FireEye’s Mandiant team have breached the network of a North American utility and turn off one of its smart meters. Over the years, the number of attacks against ICS/SCADA systems used by industrial organizations worldwide has rapidly increased.




































Let's personalize your content