Privacy Legislation Progresses in 5 More States
Data Breach Today
FEBRUARY 15, 2021
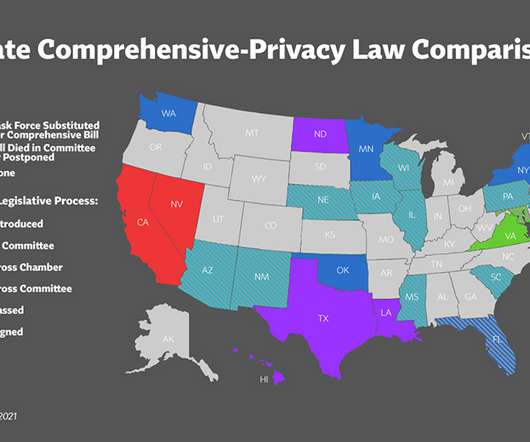
States Would Join 3 Others That Have Already Enacted Laws Five states are making progress this year toward passing privacy legislation along the lines of California's Consumer Privacy Act, according to the International Association of Privacy Professionals. Here's a status report.






































Let's personalize your content