Patch Now: Apple Bashes Bugs Being Actively Exploited
Data Breach Today
AUGUST 19, 2022
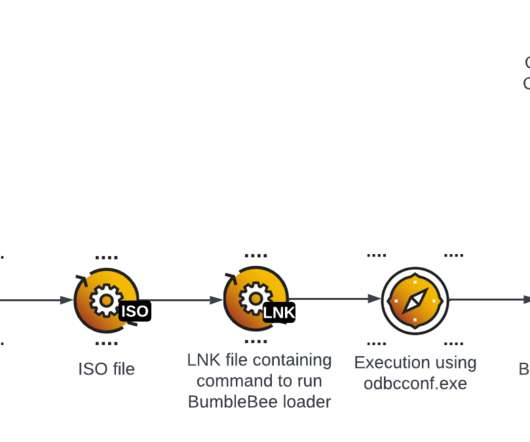
No, the Sky Isn't Falling; Yes, Do Patch Quickly to Minimize Attack Surface Calling all Apple users: It's time to once again patch your devices to protect them against two zero-day vulnerabilities that attackers are actively exploiting in the wild to take complete control of devices. While there's no need to panic, security experts advise moving quickly.









































Let's personalize your content