Carnival Cruise Ship Firm Investigating Ransomware Attack
Data Breach Today
AUGUST 18, 2020
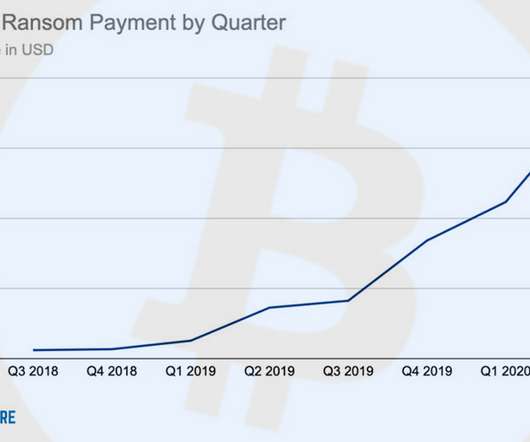
SEC Filing Warns That Guest and Employee Data Likely Compromised Carnival Corp., the world's largest cruise ship company, is investigating a ransomware attack that likely compromised guest and employee data, according its filing with the SEC. It's the company's second security incident this year.







































Let's personalize your content