Proactive Data Management: 5 Questions to Ask About Your Organization's Data
Hanzo Learning Center
FEBRUARY 9, 2022

Hanzo Learning Center
FEBRUARY 9, 2022

Schneier on Security
FEBRUARY 9, 2022
Researchers have calculated the quantum computer size necessary to break 256-bit elliptic curve public-key cryptography: Finally, we calculate the number of physical qubits required to break the 256-bit elliptic curve encryption of keys in the Bitcoin network within the small available time frame in which it would actually pose a threat to do so. It would require 317 × 10 6 physical qubits to break the encryption within one hour using the surface code, a code cycle time of 1 μ s, a reaction
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
eSecurity Planet
FEBRUARY 9, 2022
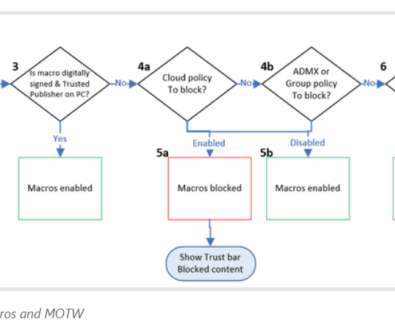
Microsoft is shutting a couple of security holes, including one that has been a favored target of attackers for years and another that the enterprise software giant recently learned could be exploited to install a malicious package. At the same time, the federal government is now adding another Microsoft flaw to its list of known vulnerabilities , giving federal agencies until Feb. 18 to patch a bug in all unpatched versions of Windows 10 and urging private and commercial organizations to remedi

Dark Reading
FEBRUARY 9, 2022
Enterprises are spending a pittance on securing their software supply chain, which makes COTS software dangerous — vulnerabilities can be "hidden" in open source components.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Micro Focus
FEBRUARY 9, 2022
History gives us plenty of reminders of the dangers of not changing with the times. The market quickly forgets those who get left behind. Derek Britton looks at what’s changing. Introduction “To change is difficult. Not to change is fatal.” – William Pollard When first published in 1955, the Fortune 500 list was following brands. View Article.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
Security Affairs
FEBRUARY 9, 2022
The US CISA warns to address a severe security vulnerability dubbed ICMAD impacting SAP business apps using ICM. Internet Communication Manager Advanced Desync (ICMAD) is a memory pipes (MPI) desynchronization vulnerability tracked as CVE-2022-22536. An unauthenticated remote attacker could exploit this issue by sending a simple HTTP request to a vulnerable instance and take over it.

WIRED Threat Level
FEBRUARY 9, 2022
A couple allegedly used a “laundry list” of technical measures to cover their tracks. They didn’t work.

Security Affairs
FEBRUARY 9, 2022
Microsoft February 2022 Patch Tuesday security updates addressed 51 flaws in multiple products, including a zero-day bug. Microsoft February 2022 Patch Tuesday security updates addressed 51 flaws in multiple products including Microsoft Windows and Windows Components, Azure Data Explorer, Kestrel Web Server, Microsoft Edge (Chromium-based), Windows Codecs Library, Microsoft Dynamics, Microsoft Dynamics GP, Microsoft Office and Office Components, Windows Hyper-V Server, SQL Server, Visual Studio

Thales Cloud Protection & Licensing
FEBRUARY 9, 2022
Not All Authentication Methods Are Equally Safe. divya. Thu, 02/10/2022 - 05:53. There is broad recognition by security leaders that stronger authentication is foundational to preventing data breaches. As recently as September 2021, US Deputy National Security Adviser for Cyber and Emerging Technologies Anne Neuberger said that multifactor authentication — which requires users to access websites and systems by entering a password and also using a second device to verify their identity — could pr

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Security Affairs
FEBRUARY 9, 2022
Google February 2022 Android security updates address two critical flaws, including a remote escalation of privilege. Google has released the February 2022 Android security updates that address two critical vulnerabilities, one of them is a remote escalation of privilege that requires no user interaction for its exploitation. The vulnerability, tracked as CVE-2021-39675 , only affects the System component of the latest version of the popular OS, Android 12. “The most severe of these issues

Dark Reading
FEBRUARY 9, 2022
Ransomware, cryptojacking, and a cracked version of the penetration-testing tool Cobalt Strike have increasingly targeted Linux in multicloud infrastructure, report states.

IG Guru
FEBRUARY 9, 2022
Check out the post here. The post Dozens of Blue Team Cheatsheets in One Documents via Dan Williams on LinkedIn appeared first on IG GURU.

Dark Reading
FEBRUARY 9, 2022
Microsoft's release of relatively sparse vulnerability information makes it difficult for organizations to prioritize mitigation efforts, security experts say.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

OpenText Information Management
FEBRUARY 9, 2022
The challenges of a global market and international competition with ever shorter innovation cycles are omnipresent. Global interactive networking paves the way for modern cloud and SaaS services, promising a shift of service delivery responsibilities out of the IT departments, freeing up capacity for the innovation necessary to thrive in the modern marketplace.

Threatpost
FEBRUARY 9, 2022
Researchers from Proofpoint have spotted a new Middle East-targeted phishing campaign that delivers a novel malware dubbed NimbleMamba.

Dark Reading
FEBRUARY 9, 2022
New feature adds a dedicated security team and support for multiple languages to prevent fraudulent access with stolen credentials.

Threatpost
FEBRUARY 9, 2022
Sonya Duffin, ransomware and data-protection expert at Veritas Technologies, shares three steps organizations can take today to reduce cyberattack fallout.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Dark Reading
FEBRUARY 9, 2022
Almost every cybersecurity product has an AI component. Here is where it's working in the real world.

Threatpost
FEBRUARY 9, 2022
The living-off-the-land binary (LOLBin) is anchoring a rash of cyberattacks bent on evading security detection to drop Qbot and Lokibot.

ForAllSecure
FEBRUARY 9, 2022
When it comes to vulnerability scanning, there are different types of scans that can be performed, and each has its benefits and drawbacks. Vulnerability scanning is an important part of security as it can help organizations identify and fix vulnerabilities before they can be exploited by attackers. Vulnerability scanning can also help organizations comply with regulatory requirements for security.

Threatpost
FEBRUARY 9, 2022
Crane Hassold, former FBI analyst turned director of threat intel at Abnormal Security, shares stories from his covert work with cyberattackers.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Archive-It
FEBRUARY 9, 2022
by Bridget Collings and Raven Germain, Web Archivists for Archive-It. The CARL 2022 Canadian Web Archiving Symposium was held January 26-27 virtually. Hosted by the Canadian Web Archiving Coalition (CWAC) and generously sponsored by the Canadian Association of Research Libraries (CARL) , the free Symposium fostered extensive community discussion about web archiving in Canada, how best to meet the evolving needs of their communities, and how CWAC can support practitioners and coordinate collectio
eSecurity Planet
FEBRUARY 9, 2022
The next few years will see a surge in channel spending. According to Jay McBain, an analyst at Forrester Research, spending on IT and telecommunications will be worth about $7 trillion by 2030. The channel is destined to land at least a third of that. Competition is fierce. With about half a million VARs currently operating and roughly 75,000 MSPs, what opportunities exist for expansion?
Security Affairs
FEBRUARY 9, 2022
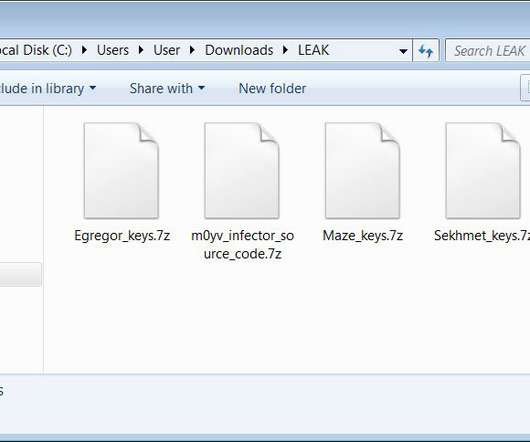
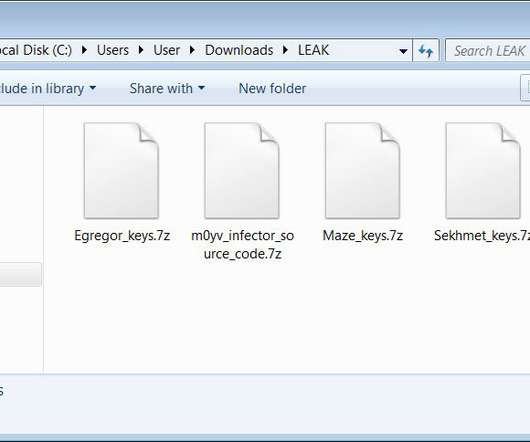
The master decryption keys for the Maze, Egregor, and Sekhmet ransomware operations were released last night on the BleepingComputer forums. The master decryption keys for the Maze , Egregor, and Sekhmet ransomware families were released on the BleepingComputer forums by the alleged malware developer. The Maze group was considered one of the most prominent ransomware operations since it began operating in May 2019.

Collibra
FEBRUARY 9, 2022
With the 14-day free Collibra Data Quality Test Drive, you can experience first-hand the power that Collibra gives you when you make data quality and observability the heart of your data strategy. The Collibra Data Quality Test Drive is a preconfigured instance of Collibra Data Quality & Observability that provides an interactive, guided tour of the platform’s various capabilities and use cases.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.
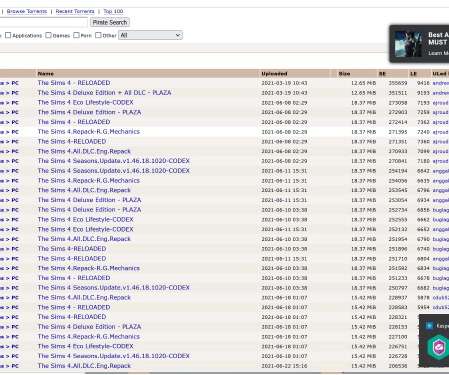
Security Affairs
FEBRUARY 9, 2022
CyberNews researchers discovered five clones of The Pirate Bay serving malicious ads to more than seven million users each month. Original Post @ [link]. CyberNews security researchers discovered five malicious domains masquerading as alternatives to The Pirate Bay. These domains were serving malicious ads to more than seven million users each month.

Krebs on Security
FEBRUARY 9, 2022
Russian authorities have arrested six men accused of operating some of the most active online bazaars for selling stolen payment card data. The crackdown — the second closure of major card fraud shops by Russian authorities in as many weeks — comes closely behind Russia’s arrest of 14 alleged affiliates of the REvil ransomware gang , and has many in the cybercrime underground asking who might be next.
Let's personalize your content