600,000 Payment Cards Stolen From Swarmshop Darknet Market
Data Breach Today
APRIL 8, 2021
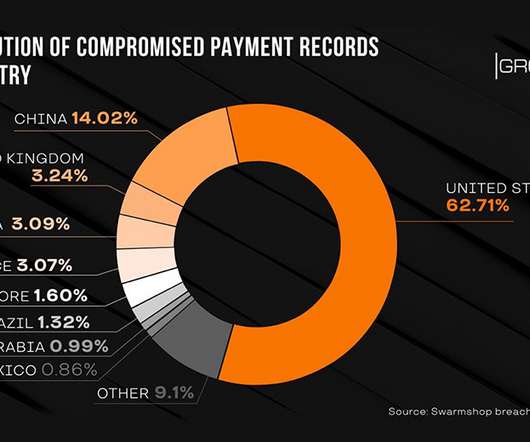
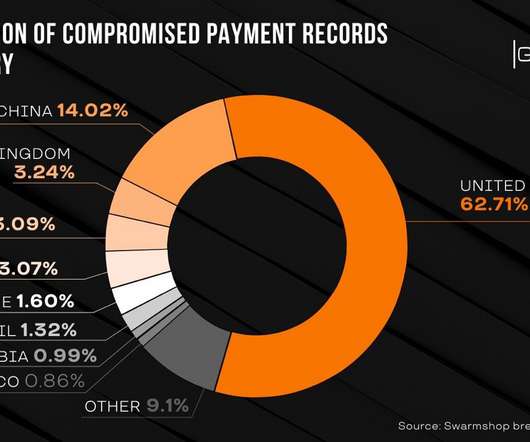
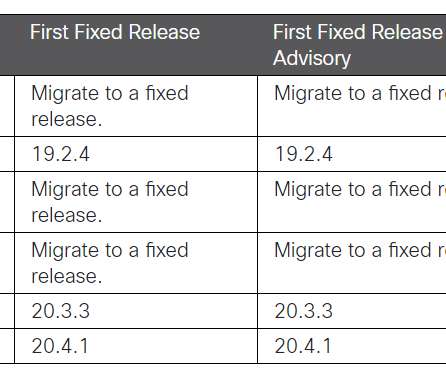
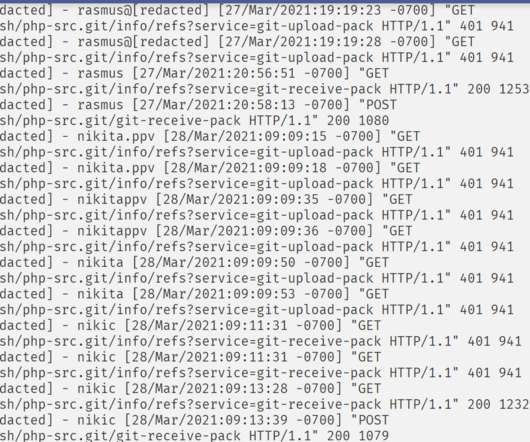
Group-IB: Administrator, Seller and Buyer Data Also Stolen For the second time in two years, the contents of the darknet payment card marketplace Swarmshop have been removed and posted to a competing underground forum, Group-IB reports. The content includes data on more than 600,000 payment cards as well as administrator, seller and buyer information.

































Let's personalize your content