TikTok Content Could Be Vulnerable to Tampering: Researchers
Data Breach Today
APRIL 15, 2020
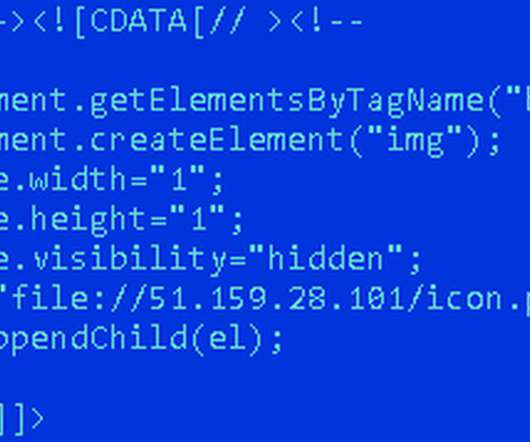
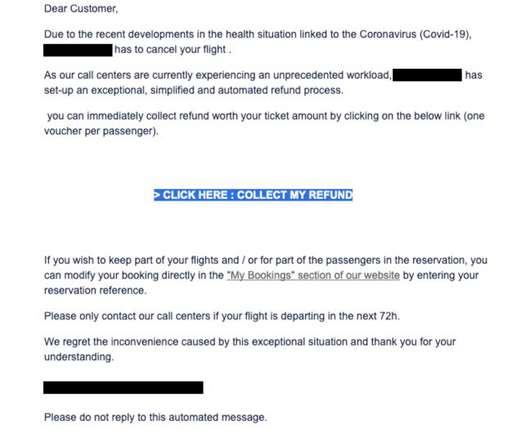
Video-Sharing Service Does Not Always Use TLS/SSL Encryption TikTok, a video-sharing service, has been delivering video and other media without TLS/SSL encryption, which means it may be possible for someone to tamper with content, researchers say. That could be especially damaging in the current pandemic environment, where misinformation and confusion abounds.






































Let's personalize your content