CDRThief Linux malware steals VoIP metadata from Linux softswitches
Security Affairs
SEPTEMBER 10, 2020
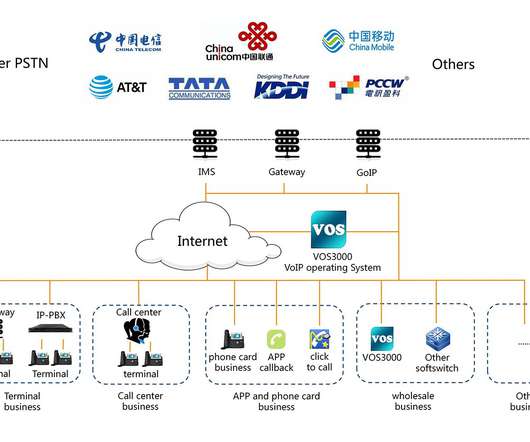
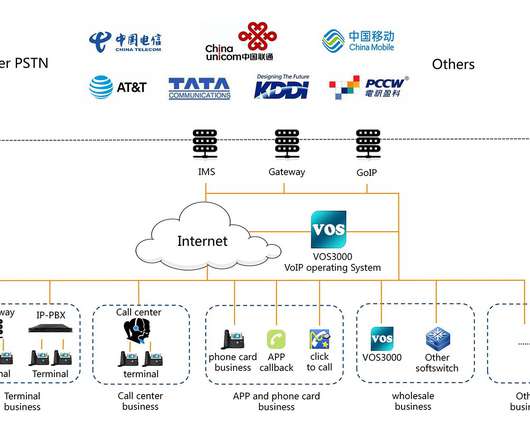
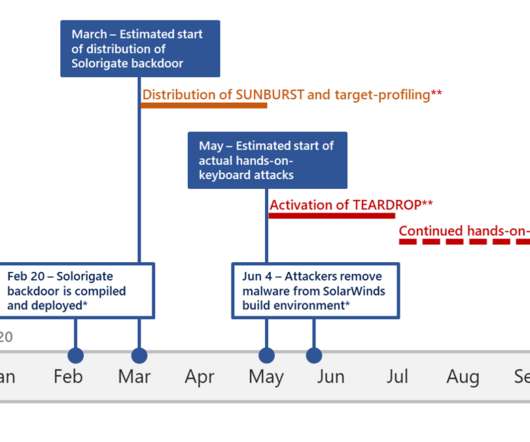
ESET researchers discovered a new piece of malware dubbed CDRThief targets a specific Voice over IP system to steal call data records (CDR). “The primary goal of the malware is to exfiltrate various private data from a compromised softswitch, including call detail records (CDR). ” reads the analysis published by ESET.




















Let's personalize your content