TicketClub Italy Database Offered in Dark Web
Security Affairs
JULY 21, 2021
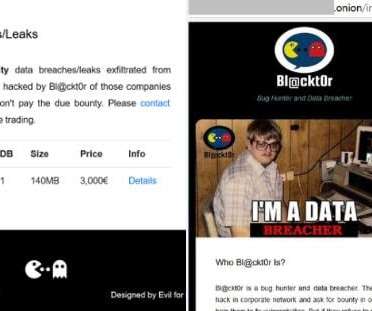
The platform lists coupons in multiple categories including health, travel, food, services, events. July 19, 2021 – The actor having the alias “ bl4ckt0r ” has published TicketClub Italy database with over 340,957 users for sale and released several meaningful data dumps which may confirm the breach.
















Let's personalize your content