How to Shop for an API Security Platform
Data Breach Today
JULY 19, 2023
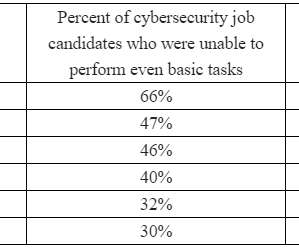
Consider Domains, Features, Ease of Integration, Scalability and Vendor Support API security platforms have become an essential part of any organization's cybersecurity strategy, but with so many options available, it can be difficult to know how to choose the right one.
















































Let's personalize your content