Snatch gang claims the hack of the Department of Defence South Africa
Security Affairs
AUGUST 22, 2023
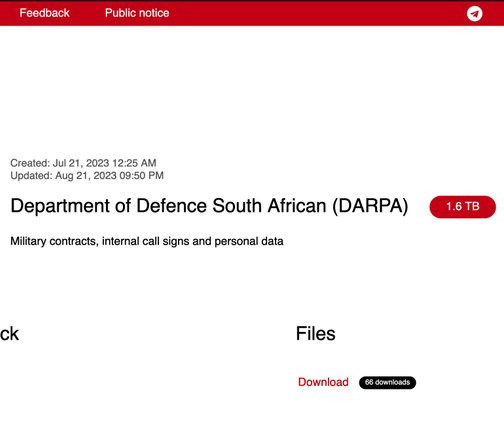
Snatch gang claims the hack of the Department of Defence South Africa and added the military organization to its leak site. The group claims to have stolen Military contracts, internal call signs and personal data, for a total of 1.6 HENSOLDT is a company specializing in military and defense electronics. TB of data.




















Let's personalize your content