Acer Philippines disclosed a data breach after a third-party vendor hack
Security Affairs
MARCH 13, 2024
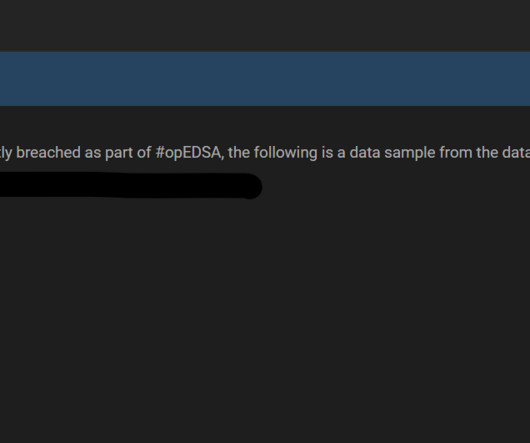
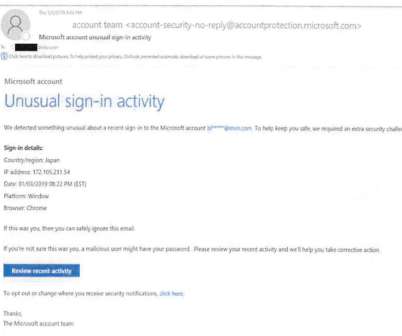
is a Taiwanese multinational company that produces computer hardware and electronics, Acer is investigating the security breach with the help of cybersecurity experts and notified the National Privacy Commission (NPC) and the Cybercrime Investigation and Coordinating Center (CICC) in the Philippines.














































Let's personalize your content