How encryption can help address Cloud misconfiguration
Thales Cloud Protection & Licensing
NOVEMBER 15, 2021
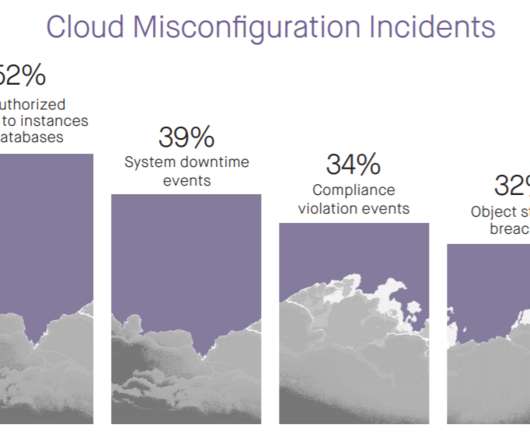
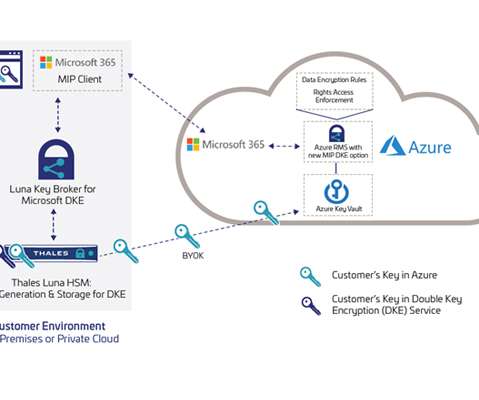
How encryption can help address Cloud misconfiguration. Cloud service providers (CSPs) try to make it simple and easy for their users to comply with data privacy regulations and mandates. Whether your organization uses cloud services or stores data across multiple clouds, each provider may protect their cloud.














































Let's personalize your content