Cryptohack Roundup: First Conviction in Smart Contract Hack
Data Breach Today
APRIL 18, 2024
Million of Cloud Services to Mine $1M of Crypto Every week, ISMG rounds up cybersecurity incidents in digital assets. Also: Nebraska Man Steals $3.5
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Data Breach Today
APRIL 18, 2024
Million of Cloud Services to Mine $1M of Crypto Every week, ISMG rounds up cybersecurity incidents in digital assets. Also: Nebraska Man Steals $3.5

Data Breach Today
JANUARY 21, 2023
Crypto Mining Campaign Targets Public Cloud Environments, Increases Security Risks Cybersecurity researchers say a Chinese for-profit threat group tracked as 8220 Gang is targeting cloud providers and poorly secured applications with a custom-built crypto miner and IRC bot.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
JUNE 20, 2018
Don’t look now but cryptojacking may be about to metastasize into the scourge of cloud services. I arrived at these conclusions after a riveting discussion with Juniper Networks ’ cybersecurity strategist Nick Bilogorskiy, one of the top analysts tracking emerging cyber threats. You can mine them, if you have a powerful CPU.

eSecurity Planet
NOVEMBER 18, 2022
Ray has wasted little time in assembling a top-notch team, which includes an unnamed cybersecurity forensics firm. ” Also read : Web3 Cybersecurity: Are Things Getting Out of Control? Crypto can also be a way to leverage cybersecurity breaches. One way is through hijacking computer resources to mine cryptocurrencies.

eSecurity Planet
SEPTEMBER 21, 2022
A retired threat actor has returned with new attacks aimed at the cloud, containers – and encryption keys. These cybercriminals are known for their creativity and ability to target cloud environments, as they introduced new techniques in 2020 that hadn’t been seen before. How to Protect Against Cloud, Container Threats.

Thales Cloud Protection & Licensing
OCTOBER 11, 2018
With a little more investigation, I found two browser extensions that were crypto mining, which fortunately uninstalled without a problem. My high schooler fessed up immediately that he installed the crypto mining extensions just to see what would happen (and to make some money). Happy Cybersecurity Awareness Month!

Security Affairs
NOVEMBER 22, 2023
Cybersecurity and Infrastructure Security Agency (CISA) added Looney Tunables Linux vulnerability to its Known Exploited Vulnerabilities (KEV) catalog. Researchers from Aqua Nautilus spotted experimental incursions into cloud environments by Kinsing actors. while processing the GLIBC_TUNABLES environment variable.
Security Affairs
JULY 29, 2020
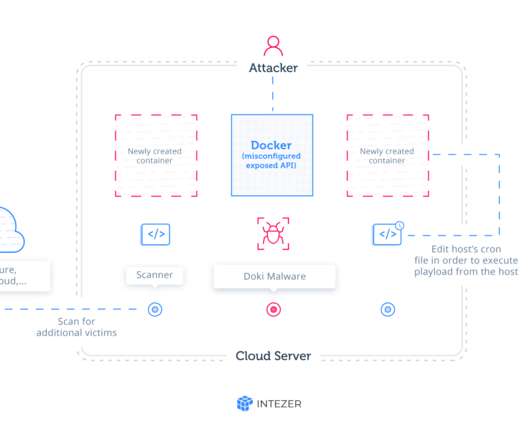
Cybersecurity researchers at Intezer spotted a new completely undetectable Linux malware , dubbed Doki , that exploits undocumented evasion techniques while targeting publicly accessible Docker servers. “ Ngrok Mining Botnet is an active campaign targeting exposed Docker servers in AWS, Azure, and other cloud platforms.

Security Affairs
APRIL 22, 2022
The Lemon_Duck cryptomining botnet is targeting Docker servers to mine cryptocurrency on Linux systems. Crowdstrikes researchers reported that the Lemon_Duck cryptomining botnet is targeting Docker to mine cryptocurrency on Linux systems. “The “a.asp” file is the actual payload in this attack. Kills known network connections.

eSecurity Planet
JUNE 16, 2022
However, basic cybersecurity tools and practices, like patching , strong passwords , and multi-factor authentication (MFA), “can prevent 80 to 90% of cyberattacks,” said Anne Neuberger, deputy national security advisor for cyber and emerging technologies, during a White House press conference in Sept. The average cost of a breach is $3.6

eSecurity Planet
AUGUST 5, 2021
Since Docker hit the scene in 2013, containers have become a primary way for developers to create and deploy applications in an increasingly distributed IT world of on-premises data centers, public and private clouds, and the edge. Insider threats can be administrators, users, or cloud service providers.
Security Affairs
MAY 4, 2022
The attacks were monitored by cybersecurity firm CrowdStrike, who discovered that the Docker Engine honeypots deployed between February 27 and March 1 were compromised and used in the DDoS attacks. “Container and cloud-based resources are being abused to deploy disruptive tools. .

ForAllSecure
APRIL 4, 2023
Incident response in the cloud. James Campbell, CEO of Cado Security , shares his experience with traditional incident response, and how the cloud, with its elastic structure, able to spin up and spin down instances, is changing incident response. That's the unique thing about clouds that's a different challenge.

Security Affairs
MAY 26, 2021
. “Most of the compromised nodes were from China and the US identified in the ISP (Internet Service Provider) list, which had Chinese and US-based providers as the highest hits, including some CSPs (Cloud Service Providers).” The malware deploys the XMRig mining tool to mine Monero cryptocurrency. Pierluigi Paganini.

Krebs on Security
APRIL 20, 2021
Mine was learning that KrebsOnSecurity is listed as a restricted competitor by Gartner Inc. So when Gartner issues a public report forecasting that worldwide semiconductor revenue will fall, or that worldwide public cloud revenue will grow, those reports very often move markets. What was the best news you heard so far this month?

Security Affairs
JUNE 1, 2019
“The script then calls a Monero coin-mining binary, darwin (detected as PUA.Linux.XMRMiner.AA), to run in the background. As with all cryptocurrency miners, it uses the resources of the host system to mine cryptocurrency (Monero in this instance) without the owner’s knowledge.” ” continues the report.
Security Affairs
MAY 17, 2022
“As for the fake cryptocurrency miner apps, their operators not only try to profit from their victims by duping them into buying fake cloud-based cryptocurrency-mining services, but they also try to harvest private keys and other sensitive cryptocurrency-related information from users who are interested in what they offer.

Security Affairs
DECEMBER 17, 2023
CISA and ENISA enhance their Cooperation CISA adds Qlik bugs to exploited vulnerabilities catalog Report: 2.6 CISA and ENISA enhance their Cooperation CISA adds Qlik bugs to exploited vulnerabilities catalog Report: 2.6
eSecurity Planet
SEPTEMBER 15, 2022
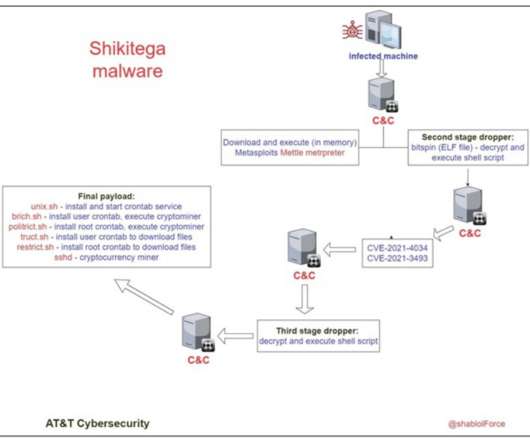
Shikitega uses legitimate cloud services to host some of its C2 (command & control) servers and a very light ELF dropper (370B) to initiate the next stages. The infamous XMRig mines Monero cryptocurrency that is known to be anonymity-focused, as it’s particularly hard to trace back. Shikitega installs XMRig version 6.17.0

eSecurity Planet
APRIL 16, 2024
Excessive access: Provides attackers with access to cloud environments via Ray root access or Kubernetes clusters because of embedded API administrator permissions. Hijacked compute: Repurposes expensive AI compute power for attackers’ needs, primarily cryptojacking, which mines for cryptocurrencies on stolen resources.

The Last Watchdog
SEPTEMBER 11, 2019
One of the promising cybersecurity trends that I’ve been keeping an eye on is this: SOAR continues to steadily mature. Security orchestration, automation and response, or SOAR, is a fledgling security technology stack that first entered the cybersecurity lexicon about six years ago. Just ask Capital One , Marriott or Equifax.
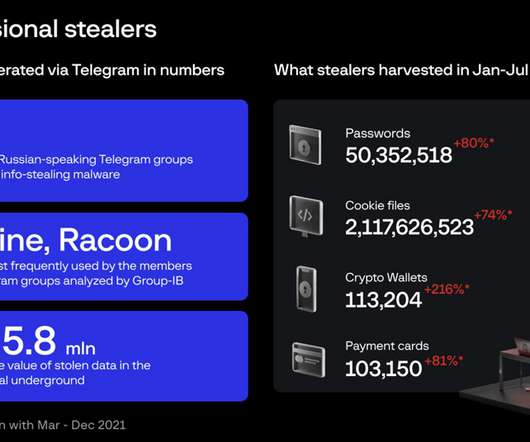
eSecurity Planet
NOVEMBER 29, 2022
Group-IB cybersecurity researchers recently identified several Russian-speaking cybercrime groups offering infostealing malware-as-a-service (MaaS), resulting in the theft of more than 50 million passwords thus far.
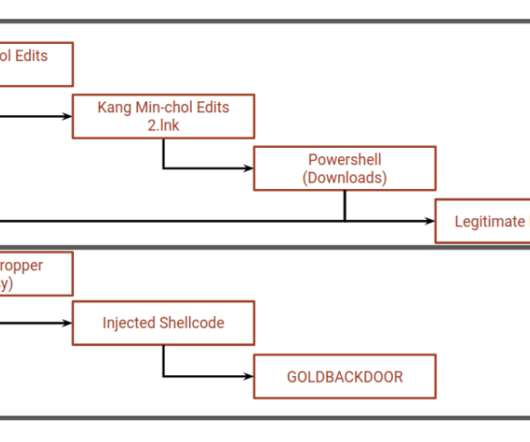
Security Affairs
APRIL 26, 2022
The phishing messages sent to the journalists contained a link to ZIP archives containing LNK files, both named ‘Kang Min-chol edits’ (Kang Min-chol is North Korea’s Minister of Mining Industries). The archive was hosted on the domain dailynk[.]us us which impersonates NK News (dailynk[.]com), ” continues the analysis.

ForAllSecure
AUGUST 18, 2021
The new Director of the Cybersecurity and Infrastructure Security Agency (CISA), Jen Easterly, opened Day 2 of Black Hat USA 2021 with a remote presentation on Hacking the Cybersecurity Puzzle. The Cybersecurity and Infrastructure Security Agency is relatively new. Easterly began by presenting her bio. There are 3.5

The Last Watchdog
DECEMBER 14, 2023
Here’s part two of Last Watchdog’s year-end tête-à-tête with top cybersecurity experts. Or Shoshani , CEO and founder, Stream Security Shoshani As 2023 ends, we’re already seeing businesses adopting technology to diagnose and detect threats to their cloud infrastructure before they occur. Part three to follow on Friday.

eSecurity Planet
AUGUST 9, 2021
Device developers at times will spend their money on features rather than security and the data on the devices often move between the devices and the cloud or on-premises data centers. IoT device security has also attracted the attention of federal government officials (see The IoT Cybersecurity Act of 2020: Implications for Devices ).

Elie
MAY 30, 2018
A very recent example of such behavior is the rise of abusing cloud services such as Google Cloud to mine cryptocurrencies in response to the surge of bitcoin price late 2017. skyrocketed past $10,000, we saw a surge of new attacks that attempted to steal Google cloud compute resources to mine. bitcoin prices.

Thales Cloud Protection & Licensing
AUGUST 30, 2019
As a result, businesses are being forced to take the issue of cybersecurity more seriously, facing it head on and putting in place the necessary steps (e.g., Do they need someone to test their cloud services and applications, or are they after a pen tester? Diving: Ethical hackers will also go dumpster diving (i.e.,

Security Affairs
MAY 2, 2021
Every week the best security articles from Security Affairs free for you in your email box.

Elie
MAY 30, 2018
A very recent example of such behavior is the rise of abusing cloud services such as Google Cloud to mine cryptocurrencies in response to the surge of bitcoin price late 2017. skyrocketed past $10,000, we saw a surge of new attacks that attempted to steal Google cloud compute resources to mine. bitcoin prices.
Security Affairs
APRIL 23, 2023
Experts warn of a large-scale cryptocurrency mining campaign exploiting Kubernetes (K8s) Role-Based Access Control ( RBAC ). Cloud security firm Aqua discovered a large-scale cryptocurrency mining campaign exploiting Kubernetes (K8s) Role-Based Access Control ( RBAC ) to create backdoors and run miners.

The Last Watchdog
MARCH 1, 2019
SOAR, if you haven’t heard, is a hot new technology stack that takes well-understood data mining and business intelligence analytics methodologies — techniques that are deeply utilized in financial services, retailing and other business verticals – and applies them to cybersecurity. Demisto launched in May 2016.

eSecurity Planet
OCTOBER 27, 2021
And finally, they’re more of a secure Wi-Fi 6 network router than an endpoint antivirus tool, but our top two overall cybersecurity vendors – Palo Alto Networks and Fortinet – now offer home and small business security solutions for those seeking the highest security possible. Also Read: Top Vulnerability Management Tools.

Thales Cloud Protection & Licensing
JULY 24, 2018
Additionally, initiatives pushing for IT modernization within the federal government mean more data is being stored in the cloud; in big data repositories; being used for IoT purposes; and being stored in containers. I think it’s worth further expanding on our cloud technology findings.

Security Affairs
NOVEMBER 29, 2018
Inception of Cloud technologies, in last few years, has completely changed the way we perceive and manage IT. A few of the hosts are running with multiple mining containers; moreover, the containers are dynamic in nature hence the data varies a bit everytime we scan the open APIs. Securi ty Affairs – cybersecurity, Hacking).

The Last Watchdog
SEPTEMBER 4, 2018
Spirent Communications , an 82-year-old British supplier of network performance testing equipment, recently decided to branch into cybersecurity services by tackling this dilemma head on. Our customers can use our cloud agents anywhere in their environment and test 24 by 7. DeSanto: Yes.

eDiscovery Daily
FEBRUARY 5, 2020
There are several interesting sessions today related to eDiscovery, Information Governance, Cybersecurity and Data Privacy. As society becomes more comfortable with the gathering and mining of sensitive personal information, the threat of AI will only increase. Build your cloud knowledge. Hope you were able to catch us there!

eSecurity Planet
APRIL 22, 2024
Adam Murayama, Field CTO of Garrison Technology, warns that “attackers know the value of targeting cybersecurity software: they not only defuse the security mechanism, but also gain the elevated system privileges and network positioning that security solutions enjoy. Instead, use secrets store services offered by the cloud providers.

Hunton Privacy
DECEMBER 19, 2013
companies to encrypt data in transit, at rest and in storage (including in the cloud); and. companies to encrypt data in transit, at rest and in storage (including in the cloud); and.

Cyber Info Veritas
AUGUST 9, 2018
As the title suggests, this post will teach you the various, beginner-to-advanced cybersecurity tips, hacks, and strategies that when applied, will minimize that no black hat hacker can turn you into a victim of cybercrimes such as data leaks, blackmail, bank account hacks, and the various forms of cybercrimes that have become so rampant today.

Thales Cloud Protection & Licensing
OCTOBER 31, 2018
Let’s take a brief look in our cybersecurity crystal ball at all three. Those wearing electronic Jason masks have recently stalked other avenues of enterprise torture such as crypto-mining. But not so fast, my little enterprise cybersecurity gremlins! Ransomware. Occurrences of ransomware of late have seemingly died down.

Security Affairs
NOVEMBER 16, 2018
In 2018 Group-IB detected five successful “51% attacks”, when attackers take control over at least 51% of mining power. Among all phishing resources, 73% can be divided into the following categories: cloud storages (28%), financial platforms (26%), and online services (19%).

Krebs on Security
JULY 30, 2019
Thompson on suspicion of downloading nearly 30 GB of Capital One credit application data from a rented cloud data server. The Twitter user “erratic” posting about tools and processes used to access various Amazon cloud instances. Paige “erratic” Thompson, in an undated photo posted to her Slack channel.

eSecurity Planet
MAY 2, 2024
The 2023 vendor surveys arriving this quarter paint a picture of a cybersecurity landscape under attack, with priority issues affecting deployment, alert response, and exposed vulnerabilities. This article details two major findings from the report: five major cybersecurity threats and prioritization problems.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content