Threat actors found a way to bypass mitigation F5 BIG-IP CVE-2020-5902 flaw
Security Affairs
JULY 8, 2020
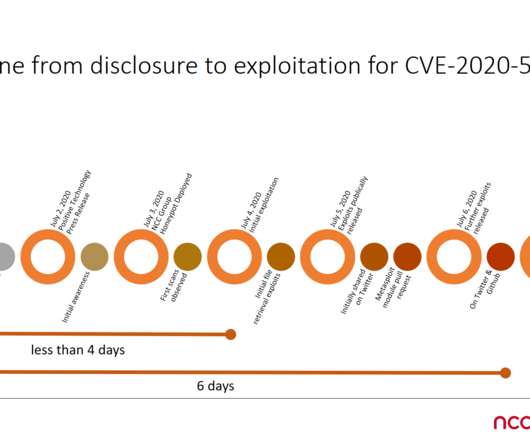
Early June, researchers at F5 Networks have addressed a critical remote code execution (RCE) vulnerability, tracked as CVE-2020-5902, that resides in undisclosed pages of Traffic Management User Interface (TMUI) of the BIG-IP product. The CVE-2020-5902 vulnerability received a CVSS score of 10, this means that is quite easy to exploit.




































Let's personalize your content