Critical Infrastructure, ICS/SCADA Systems Under Attack by Advanced Threat Groups
eSecurity Planet
APRIL 14, 2022
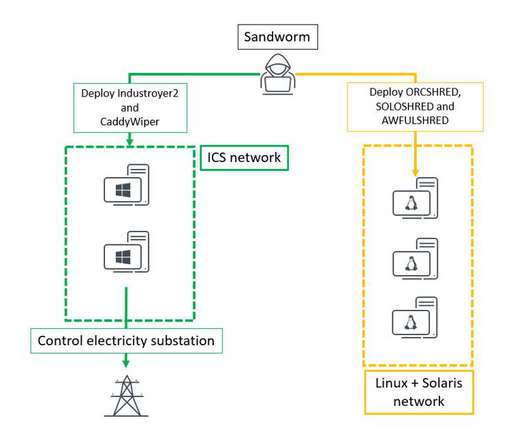
Critical infrastructure , industrial control (ICS) and supervisory control and data acquisition (SCADA) systems are under increasing threat of cyber attacks, according to a number of recent warnings from government agencies and private security researchers. Industroyer1 was specifically made to attack electric grids.




































Let's personalize your content