Phishing campaign targeted US executives exploiting a flaw in Indeed job search platform
Security Affairs
OCTOBER 4, 2023
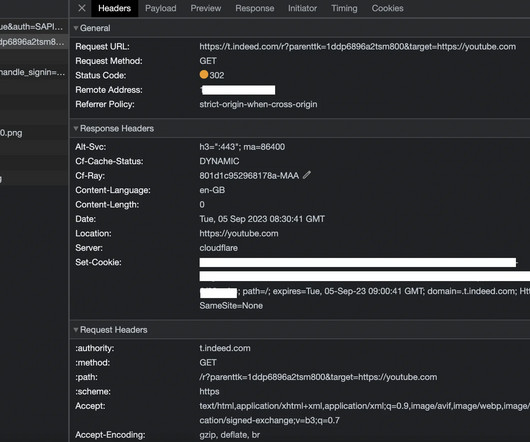
The phishing attacks were aimed at senior executives across various industries, primarily in Banking, Financial, Insurance, Property Management and Real Estate, and Manufacturing sectors. EvilProxy actors are using Reverse Proxy and Cookie Injection methods to bypass 2FA authentication – proxyfying victim’s session.






















Let's personalize your content