Google warned users of 33,015 nation-state attacks since January
Security Affairs
OCTOBER 17, 2020
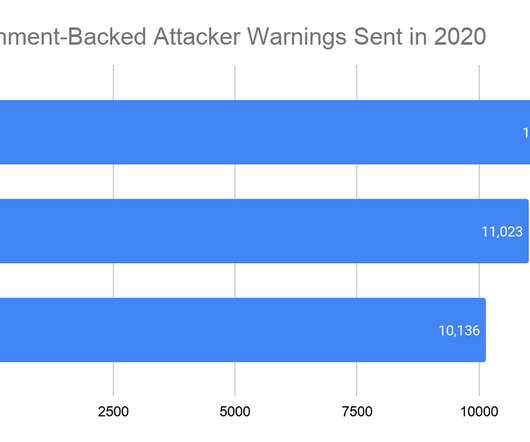
Google delivered 33,015 alerts to its users during the first three quarters of 2020 to warn them of phishing attacks, launched by nation-state actors, targeting their accounts. The IT giant pointed out that major events like elections and COVID-19 represent opportunities for threat actors. of all Gmail accounts.























Let's personalize your content