Mirai code re-use in Gafgyt
Security Affairs
APRIL 16, 2021
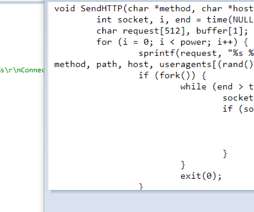
Gafgyt also uses some of the existing exploits (CVE-2017-17215, CVE-2018-10561) to download the next stage payloads, which we will discuss further on. Figure 8: GPON Router Exploit inside binary (CVE-2018-10561). Figure 11: Uptycs detection for Gafgyt I. Some of the recent Gafgyt variants (e.g., Click to see larger version.).















Let's personalize your content