QNAP Systems Patches Critical Vulnerability
Data Breach Today
MARCH 14, 2024
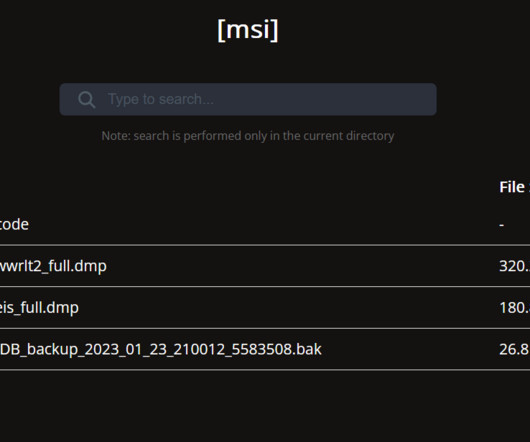
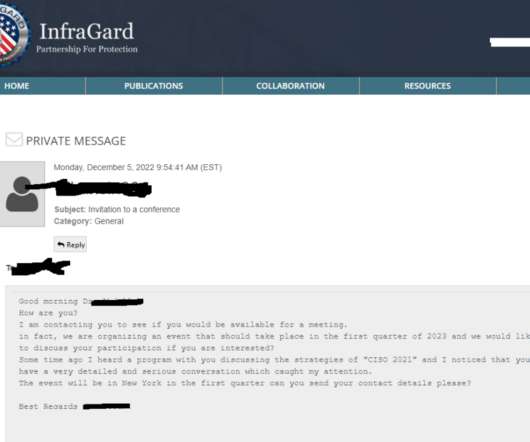
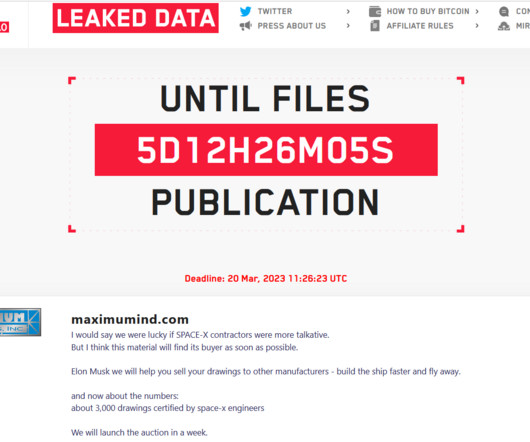
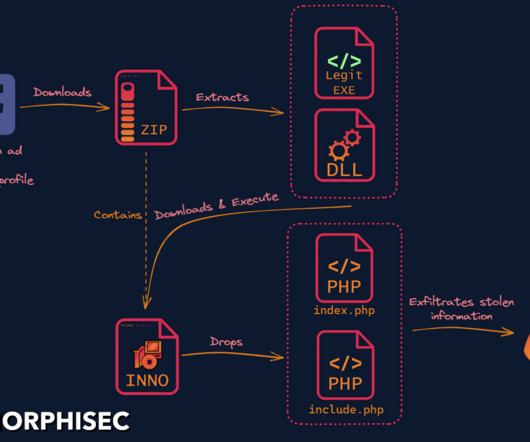
Taiwanese Hardware Manufacturer Fixes Improper Authentication Flaw QNAP Systems on Saturday released a patch for a critical bug that allows unauthorized access to devices without authentication.




































Let's personalize your content