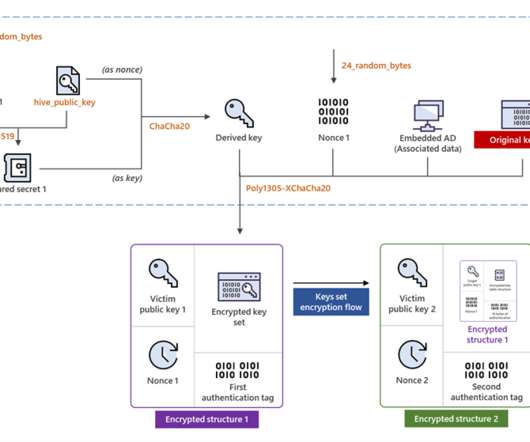
Using Blockchain for Authentication
Data Breach Today
NOVEMBER 27, 2018
In an interview, Rohas Nagpal, a chief architect at Primechain Technologies, describes how blockchain can be used for authentication and pinpoints areas where blockchain is not the ideal technology. He'll be a featured speaker at ISMG's Security Summit in Mumbai Thursday.













































Let's personalize your content