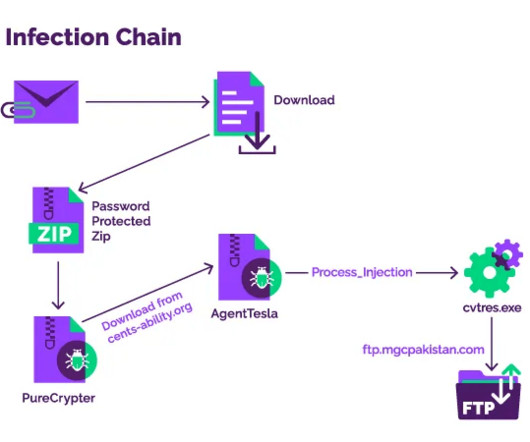
PureCrypter used to deliver AgentTesla to govt organizations
Security Affairs
FEBRUARY 27, 2023
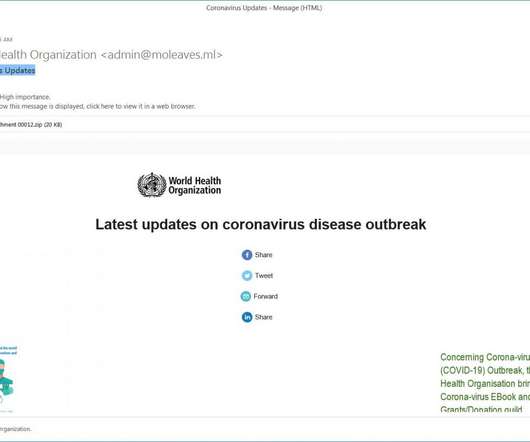
An unknown threat actor is targeting government organizations with the PureCrypter downloader, Menlo Security firm reported. Menlo Labs researchers uncovered an unknown threat actor is using the PureCrypter downloader in attacks aimed at government entities. ” reads the analysis published by Menlo Labs.




































Let's personalize your content