HackerGPT 2.0 Unveils New AI Cyber Defense Strategies
eSecurity Planet
MARCH 15, 2024
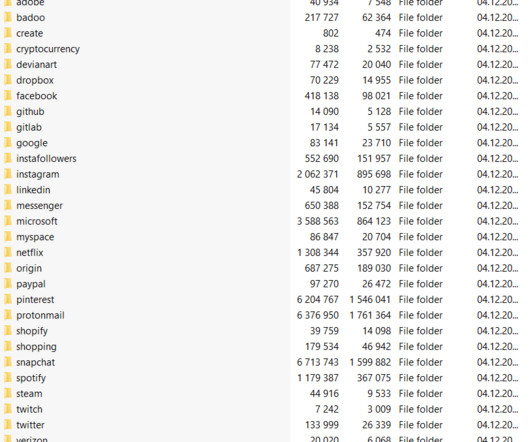
Sample HackerGPT scanning results Query Functions in HackerGPT HackerGPT provides a range of query functions such as network hacking, mobile hacking, payload creation, attack vector analysis, and vulnerability assessment. CyberChef allows you to encode and decode data, hash passwords, analyze traffic, and convert data formats.





























Let's personalize your content