Malicious file analysis – Example 01
Security Affairs
AUGUST 9, 2022
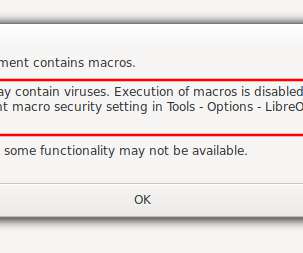
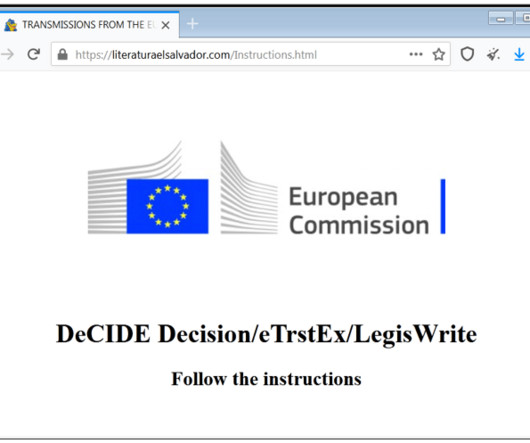
Cyber Security Specialist Zoziel Pinto Freire shows an example of malicious file analysis presented during his lecture on BSides-Vitória 2022. My objective with this series of articles is to show examples of malicious file analysis that I presented during my lecture on BSides-Vitória 2022. Microsoft Office Documents. Pdf-parser.




























Let's personalize your content