RedEnergy Stealer-as-a-Ransomware employed in attacks in the wild
Security Affairs
JULY 5, 2023
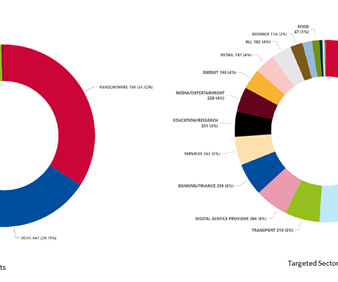
Once inside the system, this malicious variant stealthily extracts sensitive information and proceeds to encrypt the compromised files.” ” reads the analysis published by Zscaler. ” continues the analysis. The malware communicates with the command and control servers through HTTPS.































Let's personalize your content