Flaws in Realtek RTL8170C Wi-Fi module allow hijacking wireless communications
Security Affairs
JUNE 3, 2021
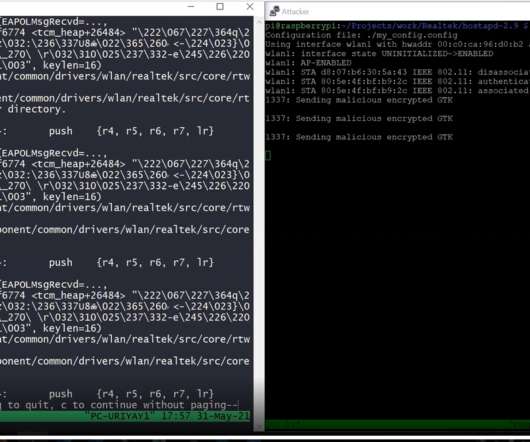
Researchers found multiple flaws in the Realtek RTL8170C Wi-Fi module that could be exploited to elevate privileges and hijack wireless communications. Researchers from Israeli IoT security firm Vdoo found multiple vulnerabilities in the Realtek RTL8170C Wi-Fi module that could allow to elevate privileges and hijack wireless communications.

































Let's personalize your content