Russia-linked hackers target Ukrainian military with Infamous Chisel Android malware
Security Affairs
AUGUST 31, 2023
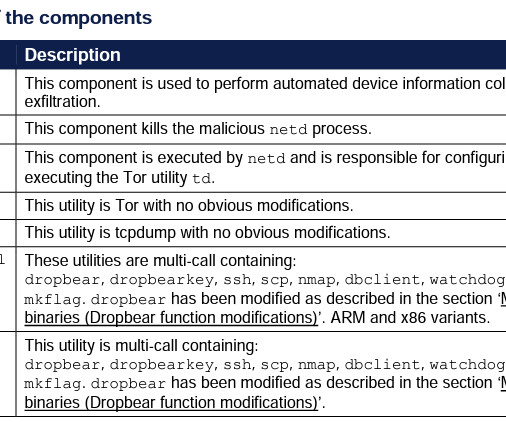
Russia-linked threat actors have been targeting Android devices of the Ukrainian military with a new malware dubbed Infamous Chisel. The Infamous Chisel malware allows threat actors to gain unauthorized access to compromised devices, scan files, monitor traffic, and steal sensitive information.






































Let's personalize your content