Microsoft Warns of North Korea's 'Moonstone Sleet'
Data Breach Today
MAY 28, 2024
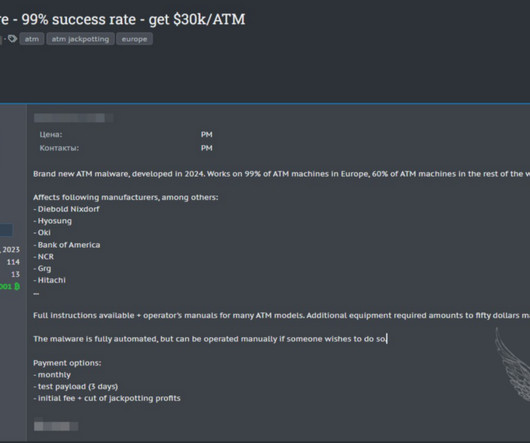
Pyongyang Threat Actor Is After Money and Information A North Korean hacking group wants to make money for the cash-starved Pyongyang regime and conduct bread-and-butter cyberespionage, say Microsoft researchers in a profile of a group they track as "Moonstone Sleet." North Korea has a well-established history of hacking for profit.




































Let's personalize your content