IoT Unravelled Part 3: Security
Troy Hunt
NOVEMBER 25, 2020
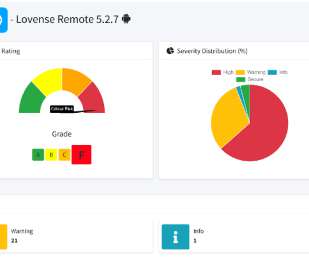
Now for the big challenge - security. The "s" in IoT is for Security Ok, so the joke is a stupid oldie, but a hard truth lies within it: there have been some shocking instances of security lapses in IoT devices. Finally, I checked my TP-Link smart plugs via the Kasa app: Uh. Let's dive into it. is that good?





















Let's personalize your content