Android devices shipped with backdoored firmware as part of the BADBOX network
Security Affairs
OCTOBER 8, 2023
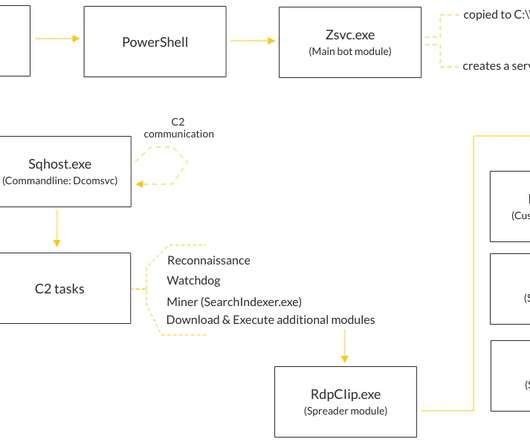
Cybersecurity researchers at Human Security discovered a global network of consumer products, dubbed BADBOX, with firmware backdoors installed and sold through a compromised hardware supply chain. ” reads the report published by Human Security. “This module is one component of PEACHPIT, the ad fraud portion of BADBOX.




















Let's personalize your content