Hackers target financial firms hosting malicious payloads on Google Cloud Storage
Security Affairs
DECEMBER 26, 2018
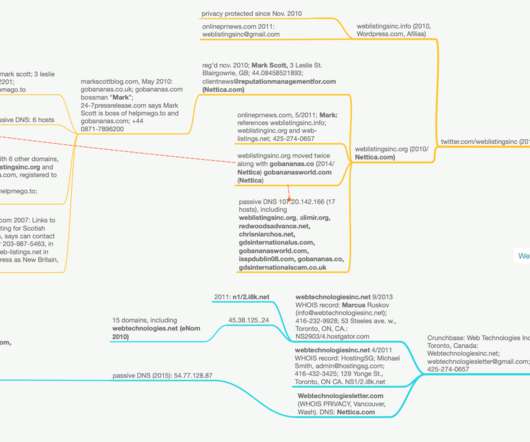
Researchers at Menlo Labs uncovered a malicious email campaign targeting employees of banks and financial services companies abusing Google Cloud Storage. “It’s an example of the increased use of “reputation-jacking”—hiding behind well-known, popular hosting services to help avoid detection.






















Let's personalize your content