Hackers target financial firms hosting malicious payloads on Google Cloud Storage
Security Affairs
DECEMBER 26, 2018
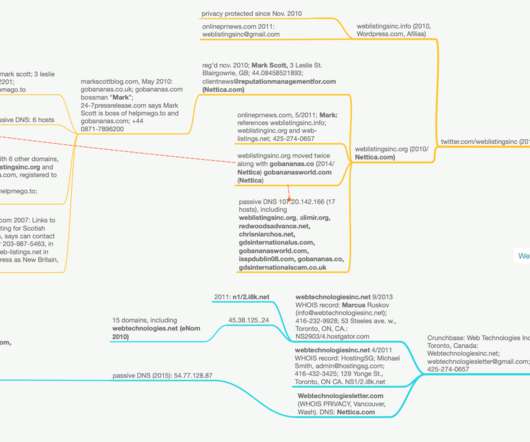
Researchers at Menlo Labs uncovered a malicious email campaign targeting employees of banks and financial services companies abusing Google Cloud Storage. With this attack scheme, threat actors are able to bypass security controls in place within targeted organizations. ” Menlo Labs concludes.




















Let's personalize your content