XDSpy APT remained undetected since at least 2011
Security Affairs
OCTOBER 2, 2020
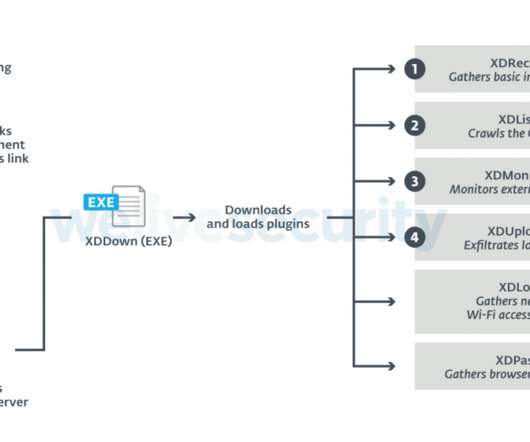
Researchers from ESET uncovered the activity of a new APT group, tracked as XDSpy, that has been active since at least 2011. XDSpy is the name used by ESET researchers to track a nation-state actor that has been active since at least 2011. The post XDSpy APT remained undetected since at least 2011 appeared first on Security Affairs.




















Let's personalize your content